

Mark Hancock discusses the politics and artistry of Janez Janša’s identity interventions in the context of their recent challenge at the Parliamentary Elections in Slovenia, in June 3rd 2018.
Ideas firmly deduced, tested against all variables and tentatively sent out into the world for appraisal by others, soon betray us as they bend to the whims of anyone they encounter. But that’s the nature of the malleable, post-digital world we live in. Ideas have to adapt and change to suit the warp and weft of the society if they are to survive in some form. How do we lock down our ideas into their final form? And what level of commitment can we expect from our ideas even if we apply intellectual property rights and that centuries-old mark of authenticity, the signature? The art world is particularly vulnerable to the conceit of signed authenticity. A signature often being the only guarantee that you’ll see any return (financial, reputational or otherwise) on your investment. If you really want to play with systems of power and bureaucracy, try altering artist names.
Davide Grassi, Emil Hrvatin and Žiga Kariž all changed their names to Janez Janša in 2007, joining the conservative Slovenian Democratic Party (SDS) at the same time, to explore the bureaucratic and political systems of their home country, Slovenia. The foundation of their actions ever since has been the question: what power exists in a name? And not just the art power system, but what political forces come into play when that name also belongs to the leader of the Slovenian Democratic Party, Janez Janša, (Prime Minister 2004 to 2008 and then again in 2012 to 2013). Incidentally, or perhaps not, Janez Janša, the politician was born Ivan Janša. The renaming of the three artists becomes a sort of double bluff when you also start to ask who the ‘real’ Janez Janša is.

It would be easy to assume that the work of Janez Janša is simply another playful, flaccid baiting of the art world and right-wing political hegemonies. All too often work that challenges the political system might as well be challenging the rules of the Italian Football League, for all the difference in the world it makes beyond the enclosed loop of the art community. There’s only so far that insulting the work of Damien Hirst with another work of art can get you. But the Janez Janša artists have chosen to pierce through the membrane of the art world and make a social difference.
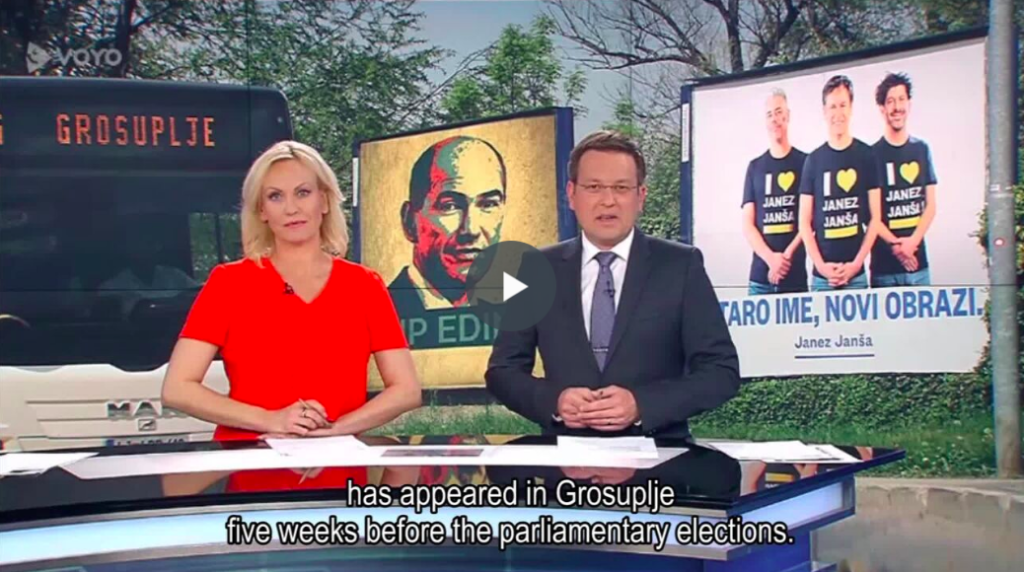
In the Slovenian Parliamentary Elections on the 3rd June 2018, one of them ran as a member of the opposition party, Levica (The Left) in Grosuplje the home district of the ex-Prime Minister, Janez Janša. In a press release, Janez Janša (the artist) said: “Running for parliament is a logical consequence of the view I have towards society. I care about what is happening. I react to things. I want to change them. (…) Society must be organized in such a way that the state begins to serve its citizens, as opposed to serving capital. Capital has no interest either for society or for art or for the individual.”
There is something inherently political in multiple authors using a single name, at least if you cast an eye over recent history. Reference points include Wu Ming, the Italian author collective that produced a number of literary works (they published a best-selling novel, Q, in 1999). They evolved from the Luther Blissett collective, whose playful, socially engaged activities defy the concept of the singular creative voice. This concept seems so alien to much of the mainstream media, particularly in Wu Ming’s home country of Italy, where they have been accused of everything from cybercrime to the less savoury aspects of rave culture. It’s this uncertainty about ownership that seems to bring a nervous lump to the throat of media and political gatekeepers. Perhaps this revolves around two questions so central to capitalism: If you’re doing nothing wrong, why hide behind a nom de plume or a collective? And, who do I send the check to, if I want to buy an Art?
On top of this, copyright issues become complex when the roster of names increases as well. Because we still want ideas to be owned, even when they are expanded through homages and pastiches. Copyright, as the attorney representing the Janez Janšas points out, is a legal construct, protecting, “original artistic (and scientific) creations, which are expressed in any way. A work is protected by copyright only if it was created by a human being (an author) and bears a stamp of author’s personality.” With work by Luther Blissett and Wu Ming, at least the authors can be understood as ‘artists’, even anonymously. Janez Janša, Janez Janša and, last but not least, Janez Janša have layered this authorship of their artwork with another layer of copyright/ownership complexity.

They refer to this work as collateral art, a phrase resonant with the phrase collateral damage, used to describe the acceptable casualties of battles. Collateral art is the acceptable damage on their ideas and projects from engagement with companies and institutions: ID cards, membership cards, the whole panoply of detritus that comes with the work. The artists want this collateral art, often customised by companies on request, to question the relationship between artworks and functional objects, “exploring post-Fordist means of production.” Any art historians still trying to shoehorn the belief of the gifted singular genius crafting his (note the gender pronoun: now discuss) solo masterpiece, probably hasn’t been paying close enough attention. The individual work of art often only becomes such with the signature of the artist attached as providence. When the work of art carries the signature of a non-artist though, can it still be brought into the art world as a valid comment on… anything? Paperwork sent to institutions by Janez Janša, and signed by an official becomes art. But whose art?
The answer, of course, is that it is their art. Whatever bureaucratic grindstone the works have been milled under, they ultimately belong back with the artists. It is they who return the work back to the art world through the exhibition. The exhibition co-produced by Moderna galerija (MG+MSUM) and Aksioma – Institute for Contemporary Art, Ljubljana, and curated by independent curator Domenico Quaranta, in 2017, was a chance to display and reflect back on ten years of work by the artists. Called the Janez Janša® exhibition, on display were works including Signatures (2007 – ongoing) which explored interventions of the Janez Janša name into public spaces, such as the Hollywood Walk of Fame (Signature, 2007), or Signature (Copacabana), in Rio de Janeiro, 2008. Playfully appearing in numerous locations around the world. Or Mount Triglav on Mount Triglav, an action performed in August 2007. This action commemorated “the 80th anniversary of the death of Jakob Aljaž; the 33rd anniversary of the Footpath from Vrhnika to Mount Triglav; the 5th anniversary of the Footpath from the Wörthersee Lake across Mount Triglav to the Bohinj Lake; the 25th anniversary of the publication of Nova Revija magazine and the 20th anniversary of the 57th issue of Nova Revija, the premiere publication of the SLOVENIAN SPRING; this was a re-enactment of Gora Triglav (Mount Triglav), by the OHO group in 1968 and the latest in a chain of re-enactments, as it was also performed by in 2004 by the Irwin Group.


The conference in the same year, Proper and Improper Names: Identity in the Information Society conference, hosted by Aksioma – Institute for Contemporary Art, Ljubljana, and curated by Marco Deseriis in 2017, invited speakers including Natalie Bookchin, Marco Deseriis, Kristin Sue Lucas, Gerald Raunig, Ryan Trecartin, Wu Ming. The subjects under discussion arose from Marco Deseriis’ book Improper Names: Collective Pseudonyms from the Luddites to Anonymous. Deseriis, as keynote speaker, talked about the genealogy of the improper name. This is Deseriis’s term for the use of pseudonyms by artist collectives, including Wu Ming (who presented a talk at the conference) and Ned Ludd, the fictional leader of the English Luddites.

Releasing your ideas out in the wild doesn’t always guarantee they will come back to you unscathed or even return at all. The works of the Janez Janša collective are sent out to corporate systems, being adapted and altered, and returned. Or at the very least offering a challenge to accepted forms of ideological structures. In the Slovenian elections on 3rd June, the Slovenian Democratic Party (SDS) won with 25% of the votes. Levica won 9.0%. The SDS is a far-right, anti-immigration party, reflecting the increasing rise of right-wing parties across Europe right now. The leader of the SDS, Janez Janša, now has the opportunity to form a right-wing government. If this happens, and by the time you read this, it may well have, it would continue the shift in European Councils members towards the right.
There’s nothing new in declaring that everything is in flux. That’s the nature of our hyper-accelerated world. But right now there is a creeping sense that The Other is also to be viewed as The Enemy. The social, political value of art has to change to mean something in what is little short of a battle for a better society for ourselves and others across the globe if it is to have any value whatsoever. Janez Janša, Janez Janša and Janez Janša’s work reflect this evolution by being part of the society around them. Being part of the electoral system reflected this challenge and desire to be part of the real world and to make art mean something more than gallery space and conference papers. If art wants to survive and continue to belong to everyone, then it needs to be part of the world we are living in right now. No one work of art ever changed the world, but it helps us unravel and see through the propaganda of systems. We all need to become Janez Janša®.
The final outcome of the recent Slovenian Elections remains uncertain as Social Democratic Party’s Janez Janša attempts to form a coalition government.
More images at Flickr – https://bit.ly/2yniHYL
More about Janez Janša – http://www.janezjansa.si/about-jj/
Featured image: Pandora’s Dropbox by Matt Bower
The Disruption Network Lab (DNL) has been presenting in Berlin some of the finest platforms for the discussion of art, hacktivism and disruption, presenting academic debates on not-so-conventional forms of thought. In their event IGNORANCE: The Power of Non-Knowledge, the second in the series Art and Evidence, various scientists and researchers discussed ignorance, not merely as a subaltern issue but as a central tool in knowledge production.
In previous events, DNL debated how ignorance is deployed as a mechanism of truth and power negotiation, mainly through the omission of the known by the means of secrecy, obfuscation and military classification. There are many forms of understanding ignorance, and this program intended to elucidate the potentialities and pitfalls within the concept. According to DNL, the first step towards approaching ignorance is to recognise it and become aware of it. As co-curator of DNL Daniela Silvestrin said (despite the paradox) that it is necessary to render the “unknown unknown into a known unknown.” The field of ignorance studies investigates the spread of ignorance, what kind of forms it takes depending on the context, how science “converts” it into probabilistic calculations of risk, and even how it can be used to push certain political, economical or religious agendas.

In the opening keynote, Matthias Gross, a sociologist and science studies scholar who has written extensively on ignorance studies, co-editing with Linsey McGoey the “Handbook of Ignorance Studies,” starts by stating that “new knowledge always creates new ignorance” and that throughout history humans have been in constant relation – acceptance, denial, resignation – with the unknown. Gross has covered how ignorance operates in different scientific milieus, namely, how risk is widely used in natural sciences as an attempt to project an idea of the future, as demonstrated in weather forecasting, but also how not knowing operates in everyday life; through secrets, the spread of false knowledge, feigning ignorance, or even through actively not wanting to know.
Gross presented a compelling body of research, exposing numerous examples in which ignorance serves the purpose as a tool to acknowledge what we don’t know in science (important in fields such as Epidemiology) or how positions of power use ignorance to manipulate public opinion within our social structures. However, the debate felt somehow stranded in an optimistic loop, where ignorance was seen mostly as a catalyst to search for further knowledge. Yet, I believe, while duelling with the binary knowledge vs ignorance, one should never forget to tackle the universalistic shape that ‘knowledge’ tends to adopt. In the end, the discussion felt insufficient, failing to examine knowledge/ ignorance from a non-hegemonic perspective when it would have been interesting to borrow criticism from postcolonial or feminist thought.

The first panel, moderated by Teresa Dillon, was deemed to shake the consensus in the room by joining the moralistic perspectives in science, the forbidden and undesired, the paranormal and the apocryphal together. Sociologist Joanna Kempner presented astonishing research focused on ‘negative knowledge,’ described as taboo, dangerous or threatening to the status quo. In an attempt to demystify the neutrality of knowledge production in sciences, Kempner interviewed various scientists to discover forbidden areas in their fields. The outcome of this research revealed that due to a fear of loss of funding and/ or sullying their reputation, scientists restrain themselves from researching illegitimate topics. For example, in Psychology one is expected not to study extra-sensory/ paranormal senses as these studies are usually associated to parasciences, a term that is in itself revealing of the hierarchies of knowledge. Kempner also exemplified how knowledge production is pressured by political interests and recalled the research-bans during the G.W.Bush government that cut funds to research related to sex and drugs under the assumption that remaining ignorant about any possible positive aspects (of recreational drug consumption) guarantees the maintenance of conservative moral values.
On the maintenance of moral values, the philosopher Jan Wieland presented an interesting experiment: “What would you do if you wouldn’t know? And what would you do if you’d know?” Giving the example of a social experiment by Fashion Revolution, a movement that calls for “greater transparency in the fashion industry”, Wieland examined consumers’ choices as they acknowledged the conditions in which clothing is actually produced. The project invokes a sentimental story with an excerpt from the daily life of a young girl living in Dhaka, Bangladesh, who works in a garment factory. Coming to terms with the girl’s story, the reactions differed — from not buying and empathically connecting with her situation to total indifference and still buying. Wieland attempts to analytically evaluate their intentions, good or bad, and how ignorance affects choices, stating that some of us might willfully remain ignorant (willful ignorance) as a way to better cope with our habits of consumption. However, I find it difficult to extrapolate these findings to a moralistic and individualistic criticism of people’s consumerist choices, since we know there is a structure that keeps consumers far from well-informed. A good example of how economy capitalises on ignorance, we know that the international division of labour is intentionally built to alienate the consumers from the “dirty” phases of production.

Jamie Allen, artist and researcher, also analyses at the economy of non-knowledge that is in the genesis of apocryphal technologies. “Do pedestrian’s crossroads’ buttons actually work?” We have all thought about this, yet has it stopped us from pressing the buttons? As long as we do not know whether a certain technology actually works, it “works”. Such an economy is boosted by acknowledging that some things remain as common ignorance. If we are not sure whether a lie detector works or not, then it can be used to incriminate — amidst ignorance, it shall produce the truth.

Informative and somewhat frightening, “Merchants of Doubt”, directed by Robert Kenner (2014), reveals how bendable ‘truth’ is in the interests of big corporations. The documentary investigates how the tobacco industry spread false information among firefighters, leading the world to believe that the domestic fires caused by cigarettes were the fault of the furniture rather than the cigarettes. This is where it goes from uncannily funny to scary. While interviewing scientists, whistleblowers and activists, the film unveils the dreadful story of corporate campaigns designed to unleash confusion and scientific scepticism among the masses, putting the life and security of millions at stake. This scepticism is not passive, thus it turns into a cynical endeavour. As corporations claim that there is no consensus surrounding issues such as global warming, conferences and books are forged to sustain their statement, while scientists who defend the existence of greenhouse gases are accused of ceding to their political biases in order to get funding for their research. What about facts? They seem to become irrelevant in the face of expensive lies.
Watch Merchants of Doubt’s trailer here.

Karen Douglas, a social psychologist, presented an empirical study of conspiracy theories whilst trying to trace a particular psychological profile of those more prone to elaborate and believe in them. Douglas used widely known conspiracy theories as examples, such as the infamous car crash that killed Princess Diana (which became a true “Schrödinger’s cat” case, instigated by the media-produced hyperreality in which Diana was both alive and dead — along with Elvis Presley) and the theory that 9/11 was orchestrated by the United States government to instigate and justify the “war on terror”. Douglas believes we are naturally hardwired to believe in conspiracy theories and sees them as a way to cope with things we are unable to answer. A socio-analytical view on conspiracy theories also seems to fail the complexity of forces that make us consider why certain theories are conspiracies and other perspectives are just theories. The issue with Douglas’ approach lies within its socio-psychological analysis, which tries to find a pathological pattern in people who believe in conspiracy theories, such as describing these people as being intentionally biased, or stating that those who tend to perceive patterns in things or believe in more than one conspiracy theory all show the “symptoms” of a conspiracy theorist. Yet, as pointed out by a member of the audience, this approach seems to lack a sensibility to the entire concept of “conspiracy theory” as a political tool to dismiss and undermine other narratives, such as narratives from an undesired other (e.g. how Russia’s government agenda is seen by the USA). Nevertheless, it is interesting to understand how these bodies of “disbelief”, should you wish to call them conspiracy theories or not, have a huge impact on our lives and inevitably our deaths (e.g. global warming, vaccination). As with apocryphal technologies, certain forms of unknown seem to crystallise as forms of knowledge – we know that we do not know and that is the way it is.

The closing panel, moderated by Tatiana Bazzichelli, has overseen our entanglement on social media and its algorithms, promising to be oracles of truth while their complex structures grow beyond our understanding. Ippolita, a group of activists and writers, warned how social media promotes emotional pornography, where our feelings are exploited by click baits in exchange for our personal data. By establishing clear metrics of interaction, like the number of likes and comments, social media creates an addictive game of forged interactivity, while we are scrutinised by biometric evaluation resultant from the same data we produce. Also analysing the manipulation of data and its weight in political agendas, Hannah Parkison, a journalist focused on digital culture, analysed Trump’s run for presidency propaganda in digital media. By using mostly social networks, such as Facebook and Twitter, Trump has kept control of his narrative without entering into risky interviews broadcast on TV. This is an effective way to get away with lies, regardless of the constant warnings from fact checkers – according to Politict 78% of what Trump said on the run for the election is not factually true. These lies spread across the internet, rendering their own truth.
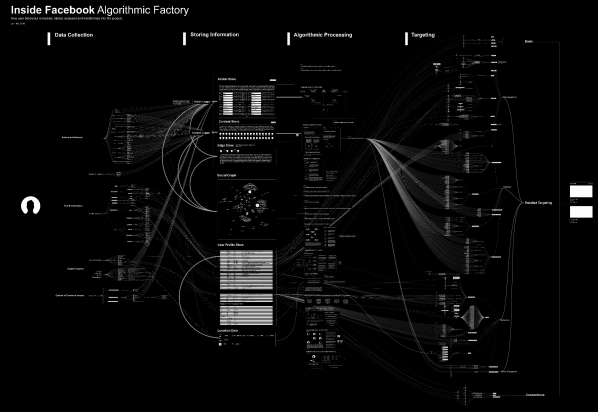
Vladan Joler, chair of New Media Department at the University of Novi Sad, presented his project in which he tries to map the tentacular structure of the Facebook algorithm, an expansive database incorporating individuals’ personal information that implies the fabrication of assumptions about potential consumers’ habits, wants and needs. Facebook was thus framed as an immaterial factory of information, the functioning of its assembly line still unknown, constantly mutating and growing. A speculative visual image of Facebook’s processes was rendered as Vladan tried to map something unknown; this mapping has similarities to the work of early cartographers. And much like early anthropological stances, the nodes of information produced have the potential to define thoughts and discussions about what we are and how we are supposed to behave. As Vladan ironically concluded, these are the tools used by the cybernet dominators – the digital monarchies that will accentuate asymmetries.
Ideas such as ‘knowledge’ find resistance and defiance from other epistemes that fall out from the western-centric productions of knowledge, such as the Amerindian ‘perspectivism’ defended by Viveiros de Castro or even the Alien phenomenologies (see Ian Bogost) that instigate the thought of non-anthropocentric ontologies. Bearing those in mind, I found that talking about the ‘dark’ side of knowledge is an invitation to dismantle and boycott its mechanisms of production, sustained in frail ideas of “truth”, “reality”, or “science”. In addition to the initial concept of ignorance, the conference provided a fertile ground for questioning the multiple ways in which humans deal with intangible phenomena, try to bypass obscurity and profit from that same obscurity. It provided insight on the relevance of knowledge to map and create reality, while bodies of power render webs of mystification of the tangible – corporations forging lies, politics of manipulation, cultural colonisation – reproducing ad nauseam epistemic violence.
The third edition of the Art and Evidence series from Disruption Network Lab, which took place on the 25th and 26th of November, wrapped up with the event TRUTH-TELLERS: The Impact of Speaking Out. TRUTH-TELLERS asks a question that could not be more crucial at the moment: “Can we trust the sources and can the sources trust us?” We have recently experienced a presidential battle between Clinton and Trump in which one of the most divisive topics were the thousands of emails sent to and from Hillary Clinton’s private email server while she was Secretary of State. A battle from which Trump left victorious despite having failed almost every fact-checking test. While Assange is forbidden to use the Internet for fear of him interfering with the presidential run in the USA, Chelsea Manning remains convicted, sentenced to 35 years of imprisonment due to her 2013 accusations of violating the Espionage Act. DNL gathered hacktivists, privacy advocates, investigative journalists, artists and researchers to “reflect on the consequences of leaking and whistleblowing from a political, cultural and technological perspective”. Unfortunately, due to a lack of funding, this could have been the very last DNL event. Let’s hope not, as these are vital, particularly in times of political despair.
I arrived at the Transmediale festival late Friday afternoon, which was hosted as usual at Das Haus der Kulturen der Welt (The House of World Cultures) in Berlin. The area where the building is sited was destroyed during World War II, and then at the height of the Cold War, it was given as a present from the US government to the City of Berlin. As a venue for international encounters, the Congress Hall was designed as a symbol of ‘freedom’, and because of its special architectural shape the Berliners were quick to call the building “pregnant oyster” [1] The exterior was also the set for the science fiction action film Æon Flux in 2005. Both past references link well with this festival’s use of the building. I remember during my last visit, in 2010, standing outside the back of the building watching an Icebreaker cracking apart the thick ice in the river. The sound of the heavy ice in collision with the sturdy boat was loud and crisp. This sound has stayed with me so that whenever I hear a sound that is similar I’m immediately transported back to that point in time. Unfortunately, this time round there was no snow, instead the weather was wet, warm and slighty stormy.
Last year’s festival explored the marketing of big data in the age of social control. This year, the chosen format was entitled conversationpiece, with the aim of enabling a series of dialogues and participatory setups to talk about the most burning topics in post-digital culture today. To give it grounding and historical context the theme was pinned to the “backdrop of different processes of social transformation, 17th and 18th century European painters perfected the group portrait painting known as the “Conversation Piece” in which the everyday life of the aristocracy was depicted in ideal scenes of common activity.” In recent years the festival has scafolded its panels, workshops and keynotes to grand, central themes to guide its peers and visitors, along with a large-scale curated exhibition. If we view the four interconnected thematic streams- Anxious to Act, Anxious to Make, Anxious to Share and Anxious to Secure – we might guess that the festival curators are also anxious to save all the resources (and celebrations) for next year, which is after all, Transmediale’s 30th birthday.
So, I was curious to see how my brief time here would unfold…
This review is focused on the hybrid event Off-the-Cloud-Zone. It featured presentations, talks and workshops, starting at 11 am, going on until 8pm. Hardcore indeed. It demanded total dedication, which unfortunately I was not able to give. However, I did offer my attention to the rest of the proceedings from lunch time until the end. It was moderated by Panayotis Antoniadis, Daphne Dragona, James Stevens and included a variety of speakers such as: Roel Roscam Abbing, Ileana Apostol, Dennis de Bel, Federico Bonelli, James Bridle, Adam Burns, Lori Emerson, Sarah T Gold, Sarah Grant, Denis Rojo aka Jaromil, George Klissiaris, Evan Light, Ilias Marmaras, Monic Meisel, Jürgen Neumann, Radovan Misovic aka Rad0, Natacha Roussel, Andreas Unteidig, Danja Vasiliev, Christoph Wachter & Mathias Jud, and Stewart Ziff.
The Off-the-Cloud-Zone day event was a continuation of last year’s offline networks unite! panel and workshops. Which also originated from discussions on a mailing list called ‘off.networks’ with researchers, activists and artists working together around the idea of an offline network operating outside of the Internet. The talks concentrated on how over recent years there has been a growing scene of artists, hackers, and network practitioners, finding new ways to ask questions through their practices that offer alternatives in community networks, ad-hoc connectivity, and autonomous systems of sensing and data collecting.
Disillusionment with the Internet has spread widely since 2013, when Edward Snowden the US whistleblower leaked information on numerous global surveillance programs. Many of these programs are run by the NSA and Five Eyes with the cooperation of telecommunication companies and European governments raising big questions about privacy and exploitation of our online (interaction) data. This concern is not only in relation to spying corporations, dodgy regimes and black hat hackers, but also our governments. “The idea of privacy has been flipped on its head. People don’t have to disclose their own information voluntarily anymore; it’s being taken from them regardless of their wishes.” [2] (Nowak 2015)
“The NSA’s principal tool to exploit the data links is a project called MUSCULAR, operated jointly with the agency’s British counterpart, the Government Communications Headquarters . From undisclosed interception points, the NSA and the GCHQ are copying entire data flows across fiber-optic cables that carry information among the data centers of the Silicon Valley giants.” [3] (Gellman and Soltani, 2013)
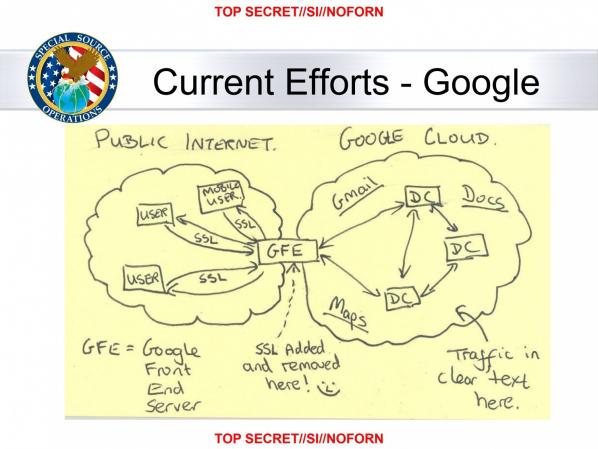
The above slide is from an NSA presentation on “Google Cloud Exploitation” from its MUSCULAR program. The sketch shows where the “Public Internet” meets the internal “Google Cloud” where user data resides. [4]
A legitimate concern for anyone wishing to read the contents of the leaked Snowden files, is that they will be spied upon as they do so. Evan Light has been working on finding a way around this problem, and at the Off-the-Cloud-Zone day event he presented his project Snowden Archive-in-a-Box. A stand-alone wifi network and web server that permits you to research all files leaked by Edward Snowden and subsequently published by the media. The purpose of the portable archive is to provide end-users with a secure off-line method to use its database without the threat of surveillance. Light says, usually the wifi network is open, but users do have the option to make their own wifi passwords and also choose their encryption standard.

Snowden Archive-in-a-Box is based on the PirateBox, originally created by David Darts who made his in order to distribute teaching materials to students without the hassle of email. It is based on a RaspberryPi 2 mini-computer and the Raspbian operating system. All the software is open-source and its most basic setup can run on one RaspberryPi. In his talk Light said that a more elaborate version would use high-quality battery packs and this adds power for autonomy, along with the wifi sniffer that is running on a secondary RaspberryPi and a flat-screen for playing back IP traffic. If you’re interested in building your own private, pirate Archive-in-a-Box, visit Light’s web site for instructions on how to.

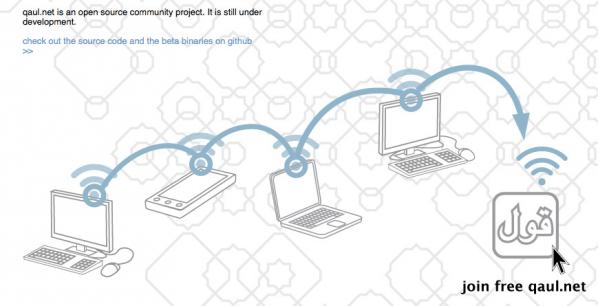
Christoph Wachter’s and Mathias Jud’s work, directly engages with refugees and asylum seeker’s social situations, policies, and the migrant crisis. They’ve worked together on participatory community projects since 2000 and have received many awards. For instance, take a look at their digital communications tool qaul.net which is designed to counteract communication blackouts. It has been used successfully in Egypt, Burma, and Tibet, and works as an alternative to already existing government and corporate controlled communication pathways. But, it also offers vital help when large power outages occur, especially in areas in the world suffering from natural disasters. The term qaul is Arabic and means ‘opinion, say, talk or word’. Qaul is pronounced like the English word ‘call’.

It creates a redundant, open communication code where wireless-enabled computers and mobile devices can directly initiate a fresh, unrestricted and spontaneous network. This includes the enabling of Chat, twitter functions and movie streaming, independent of Internet and cellular networks. It is also accessible to a growing Open Source Community who can modify it freely.
Wachter and Jud also discussed another project of theirs called “Can You Hear Me?”, a WLAN / WiFi mesh network with can antennas installed on the roofs of the Academy of Arts and the Swiss Embassy in Berlin, which was located in close proximity to NSA’s Secret Spy Hub. These makeshift antennas made of tin cans were obvious and visible for all to see. The Academy of Arts joined the project building a large antenna on the rooftop, situated exactly between the listening posts of the NSA and the GCHQ to enable people to directly address surveillance staff listening in. While installing the work they were observed in detail by a helicopter encircling overhead with a camera registering each and every move they made, and on the roof of the US Embassy, security officers patrolled.

“The antennas created an open and free Wi-Fi communication network in which anyone who wanted to would be able to participate using any Wi-Fi-enabled device without any hindrance, and be able to send messages to those listening on the frequencies that were being intercepted. Text messages, voice chat, file sharing — anything could be sent anonymously. And people did communicate. Over 15,000 messages were sent.” [5] (Jud 2015)
A the end of their presentation, they said that they will be implementing the same system at hotspots deployed in Greece by the end of the month. And I believe them. What I find refreshing with these two, is their can do attitude whilst dealing with political forces bigger than themselves. It also gives a positive message that anyone can get involved in these projects.
And then, it was the turn of the well known team at Dyne.org to discuss a project of theirs called Dowse, which is ‘The Privacy Hub for the Internet of Things’. They said (taking turns, there was about 5 of them) that the purpose of Dowse is to perceive and affect all devices in the local, networked sphere. As we push on into the age of the Internet of Things, in our homes everything will be linked up.
“Those bathroom scales and home thermostats already talk to our smartphones and in some cases think for themselves.” [6] (Nowak 2015)
As these ubiquitous computers communicate to each other even more, control over these multiple connections will be essential. We will need to know how to interact beyond the GUI interfaces and think about who has access to our private, common and public information. A whole load of extra information will be available without our consent.
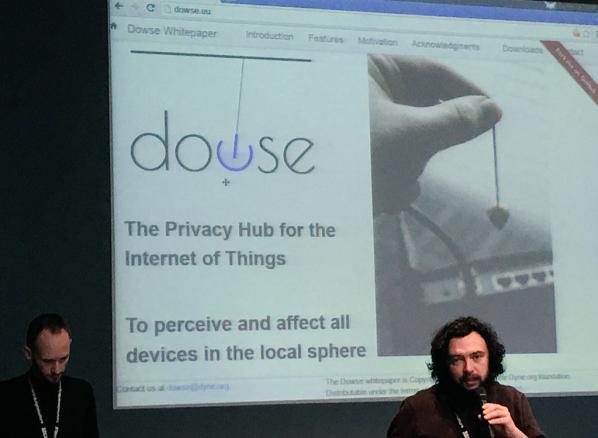
Dowse was conceived in 2014 as a proof of concept white paper by Denis Rojo aka Jaromil. Early contributors to the white paper and its drafting process includes: Hellekin O. Wolf, Anatole Shaw, Juergen Neumann, Patrick R McDonald, Federico Bonelli, Julian Oliver, Henk Buursen, Tom Demeyer, Mieke van Heesewijk, Floris Kleemans and Rob van Kranenburg. I downloaded the white paper and is definitely worth reading.
The Dowse project aims to abide to the principles stated in the Critical Engineers Manifesto, (2011). Near the very end of the talk they announced to the audience an open call for artists and techies everywhere to get involved and jump into the project to see what it can do. This is a good idea. If there is no community to make or break platforms, hardware and software, then there is a limited dialogue around the possibilties of what a facility realistically might achieve. Not just that, they want artists to make art out of it. I know there are some pretty clever tech-minded geeks out there, who will in no doubt take on the challenge. However, once those who are not so literate in the medium are able to exploit the project, it will surely fly. It’s going to be interesting, because if you look at the 3rd point in the Critical Engineers Manifesto, it says “The Critical Engineer deconstructs and incites suspicion of rich user experiences.” I’m thinking, that this number 3 element needs to treated with caution. If they really wish to open it up to a diverse user base, to engage with its potentialities, creatively and practically; thus, allow new forms of social emancipation to evolve as ‘freedom with others’. There needs to be an active intent to avoid a glass ceiling based on technical know-how. It’s a promising project and I intend to explore it myself and see what it can do and will invite other people within Furtherfield’s own online, networks to join in and play, break, and create.
Our final entry is the Sarantaporo Project which is situated in the North of Greece. A village in the mountains just west of Mount Olympus in Central Greece close to Thessaloniki, Macedonia and Larisa. The country has been in recession for over 6 years now, and many communities have had to create alternative ways of working with each other in order to survive the crisis. Over this troubling period, new forms of grass-roots coexistence, solidarity and innovation have evolved. The Sarantaporo Project is an impressive example of how people can come together and experiment in imaginative ways and exploit physical and digital networks.

Even before the economic crisis the region was already hit by poverty, and with the added pressures of imposed Austerity measures, life got even tougher. All the young were leaving and then migrating to the cities or abroad. Before the project in Sarantaporo, there was no Internet nor digitally connected networks for local people to use. This situation contributed to the digital divide and made it difficult to work in a contemporary society, when so many others in the world have been using technology to support their civic, academic and business for so many years already.
“In Greece, where unemployment reaches 30% in all ages and genders, and among the youth overpasses 50%, immediate solution for the “social issue” is more than urgent.’ [7] (Marmaras).
“Besides maintaining the network in a DIWO (Do It With Others) manner, and creating an atmosphere of cooperation among far-flung communities that were previously strangers, the Sarantaporo network is incorporating different groups of people into the community, like Farmer’s Cooperatives and techies. It is also creating an intergenerational space for learning.” [9] (Bezdommy 2016)

To resolve this issue a group of friends decided to deal with this problem by setting up a community D.I.Y wireless network to provide free internet access to 15 villages in the municipality of Elassona. “Sarantaporo.gr is an open source wireless mesh networking system that relies greatly on voluntary work both for its development and maintenance. Some volunteers are involved in the project by simply installing an antenna on their roof. Others, more actively engaged with the project, are responsible for sustaining the network by hosting meetings and answering technical questions.” [8] (Kalessi 2014) The audience was presented with snippets from a film made by the filmmaking collective Personal Cinema, about the project. It was made so the story of Sarantaporo’s DIY wireless network gets a wider reach, and that others are also inspired to do similar projects themselves.
These projects are dedicated to creating socially grounded and engaged alternatives to the proprietorial, networked frameworks that currently dominate our communication behaviours. These proprietorial systems, whether they are digital or physical are untrustworthy, and control us in ways that reflect their top-down demands but not our common needs. This reflects a wider conversation about who owns our social contexts, our conversations, our fields of practice, the structures we use, the land, the cables, our history, and so on.
Looking at the state of the planet right now you’d be forgiven for betting on a future not far from the director Neill Blomkamp’s vision in the sci-fi movie Elysium where, in the year 2159, humanity is sharply divided between two classes of people: the ultra-rich whom live aboard a luxurious space station called Elysium, and the rest who live a hardscrabble existence in Earth’s ruins. However, in the Off-the-Cloud-Zone talks we encountered an ecology of strategies to protect our own indegenous cultures from the crush of neo-liberalism, we felt part of a grounded movement discovering new conversations and new methodologies that may provide some protection against future colonisation. Perhaps there is a chance, we can build and rebuild stronger relations with each other, beyond: privilege, nation, status, gender, class, race, religion, and career.
The festival this year was less structured and more nuanced than usual. It gave conversation a greater role and a deeper social context, and opened up the process for the many to connect with the ideas being explored. The whole affair seemed to be slowed down and less caught up in the hyper-macho trappings of accelerationism. It seemed less neurotic and spending less effort to impress. I’m sure, next year, on it’s 30th anniversary, all will be sharp and amazing. However, I liked this less glossy, more messy version of Transmediale and I hope it manages to impress the wrong people again, and again.
Featured image: The facade of Kunstquartier Bethanien. Image by Nadine Nelken.
After a full year of events focusing on several topics, from drones to surveillance, cyberfeminism to hacktivism, or even the famous Technoviking and a hot debate on the politics of the Porntubes, the Disruption Network Lab wraps up 2015 with its event STUNTS, focusing on political stunts, interventions, pranks and viralities. It was a year of great success for the DNL and proof of that was a full house, in the middle of a cold Berlin winter, full of people eager to take part of this last gathering on art research, hacktivism and disruption.
Just at the entrance, in the castle-like facade of Kunstquartier Bethanien, the Free Chelsea Manning Initiative projected a video including phrases of support, denouncing the system that violently charges against all the whistleblowers who bravely stand against state-crime. Chelsea Manning, sentenced in August 2013 to 35-years of imprisonment, turned 28 years old on the 17th December. The initiative took the occasion to celebrate her anniversary but also to remind us of her cause and of how vulnerable whistleblowers are under the purview of “justice”.

Peter Sunde, one of the founders of Peter Bay, has recently given an interview stating “I have given up” when asked about the current state of free and open internet. The pessimistic tone that might loom among hacktivism has its reasons. With a growing and raging state surveillance, invigorated politics of fear veiled as anti-terrorism propaganda, or the alienating neoliberal order, the seemingly scarce possibilities to fight back can be easily overtaken by a sense of hopelessness. Yet, the proposal of STUNTS claims the possibility of new futures; suggesting that new artistic militancies and political subversions of neoliberal networked digital technologies, hoping to provide a glimpse of another world. What can be done? There’s still a lot to be done.

The opening keynote was reserved to John Law, original member of the Suicide Club and Cacophony Society, and one of the initiators of the Burning Man Festival, who gave an inspiring speech condensing 40 years of disruptive movements in the city of San Francisco. Law highlighted how important it was to live in San Francisco, a well-known refuge for many weirdos, hippies and punks, and how the city served as fertile ground for the foundation of many movements of disruption, such as the Suicide Club or the Cacophony Society.

The Suicide Club, born from a course at the Free School Movement (also known as Communiversity) in the late 70s, was one of the pioneers with its events of urban exploration, street theatre and pranks. For several years, its members engendered actions of occupation and appropriation of public spaces, aiming to subvert the order of these spaces and highjack the authorities. Later on, some of its members founded the Cacophony Society which followed the same footsteps, creating social experiments and stunts, which according to Law didn’t necessarily mention being political but instead playful acts of liberation from the norm. Yet, in an age of overwhelming neoliberal labour exploitation, we can wonder if having fun among the working class isn’t already a political act. As Law said, “the events were illegal but not immoral” reminding everyone that in ethics and politics of disruption, right and wrong should never be defined by law. It seems that disruption is intrinsically political in the sense it questions the ruling order while also being an emancipatory act of dissidence.
PANEL: STUNTS & DUMPS – THE MAKING OF A VIRAL CAUSE

The panel, moderated by Ruth Catlow, one of the founders of Furtherfield, included a group of four hacktivists and disruptors, two of whom claimed to have once been Luther Blissett, an open-pseudonym used by several artists and activists as an hoax who has taken credit and responsibility over several stunts and pranks over the past 20 years. Following the thread of adopting an emancipatory praxis in the demand for privacy, M.C.McGrath presents the Transparency Toolkit. Motivated to refuse of data collection and the brute quantification that intelligence and corporations enforce as an interpretative lens for evaluating people’s lives, with this toolkit McGrath intends to facilitate the access to a database that allows journalists and civilians to surveil the surveyors. Providing easy access to personal data of the intelligence community, he gives intelligence a taste of its own poison. In response to the predictive justice portrayed by nowadays algorithmic supremacy, the Transparency Toolkit disturbs the power asymmetry while possibly enabling for even some form of critical mob justice.

Andrea Natella, creative director of guerrigliamarketing.it and KOOK Artgency, seeks for justice by creating elaborate hoaxes that corrupt corporate advertisement. Hoaxes such as the fake air company Ryanfair which claimed to “welcome aboard refugees” under the Geneva Convention, enabling refugees to fly without a visa. The ingenious mockery resulted in a flamed response from the ‘real’ company debunking the advertisement while at the same time it has received a great attention from the media, resulting in a broader public discussion on the refugee situation. Once again, Natella presents us with the power of disruption by taking advantage of tools used by the prevailing order.

The undergraduate in Computer Sciences Mustafa Al-Bassam has gained notoriety for being a part of LulzSec, a computer hacking group responsible a number of high profile attacks, resulting in being legally banned from the Internet for two years. From an early age Mustafa focused his time in the creation of tools to unmask the tenacious mechanisms of domination. From ironically proving the negative correlation between tests scores and the amount of assigned homework to denouncing violations of online privacy and security perpetrated by state agencies such as the FBI, Mustafa has been a main character in the defence of human rights in the post-digital era.
To close the panel, Jean Peters, co-founder of the Peng! collective, shifts the perspective of the debate. What if instead of blaming or attacking members of intelligence we could provide them the tools to liberate them from their own institutions? Recognising that within the intelligence community resides a great number of whistleblowers, Intelexit, which started as a hoax, is now an initiative that helps people leave the secret service and build a new life. Aimed specially at members of agencies such as CGHQ or NSA, Intelexit offers safe and encrypted channels of communication through which intelligence members can get access to legal and moral support. Without the intention of dismissing responsibility of these members, claiming some banality of evil, by emancipating intelligence members Intelexit conceives another possibility to disrupt the system from within.
CELEBRATING AT SPEKTRUM

With an incredible array of playfully disruptive tools and practices, the ending tone of the panel is of hope and optimism. Maybe this is the kind of optimism that inspired Chuck Palahniuk into writing the Fight Club, clearly influenced by the Cacophony Society of which he was a member. Optimistic disruption seems to pave way to new worlds of possibilities, into a new future envisioned with the help of DNL.
To close STUNTS in an even more optimistic way, the celebration of a year of DNL was at SPEKTRUM, another outstanding initiative in Berlin and another example of success. After less than a year of activity, SPEKTRUM, an open space that aims to link art and science, has already gathered a solid reputation in the field along with a trustee community of followers and participants. While we cross fingers for another year of funding for DNL, SPEKTRUM will continue to offer a rich program of concerts, performances, installations and debates.
Last Review – PORNTUBES: Reveals All @Disruption Network Lab, Berlin. By Pedro Marum, 2015
http://furtherfield.org/features/porntubes-reveals-all-disruption-network-lab-berlin
Featured image: Image from Joel Bakan: The Panopticon Power of the new media. Adbusters Jan 2012.
Marc Garrett and Ruth Catlow interview McKenzie Wark ahead of his keynote speech for Transmediale 2015 in Berlin this year.
It’s ten years since McKenzie Wark published his influential book, A Hacker Manifesto. Divided into 17 chapters, each offers a series of short, numbered paragraphs that mimic the epigrammatic style of Guy Debord’s The Society of the Spectacle. Wark then published, amongst others, a series of critically engaging books such as Gamer Theory and the Spectacle of Disintegration. Ruth Catlow and Marc Garrett from Furtherfield ask Wark how things have changed since these publications, focusing on how our everyday lives have been infiltrated by competitive game-like mechanisms that he described more than a decade ago.
Furtherfield: You published the experimental writing project Gamer Theory first as a book in 2006 and then in 2007 with a specially revised 2.0 version online.

Mckenzie Wark: Yes, although I think the network book version is mostly broken now. Good thing there’s a dead-tree format back-up!
F: In it you argue that we’re living in a world that is increasingly game-like and competitive. Also that computer games develop a utopian version of the world that realizes the principles of the level playing field and reward based on merit; whereas in the world, this is promised, but rarely realized.
MW: Yes, I think one way of thinking about certain games is that they are a fully realized neo-liberal utopia, which actually gives them some critical leverage of everyday life, which is a sort of less-real, only partially realized version of this, where the playing field is not level, where the 1% get to ‘cheat’ and get away with it.
F: You also talk of the “enclosure of the world” within the “gamespace” where the logics of the game are applied as the general patterns of organization in the world. And this happens as we adapt to the allegorical forms of contemporary games media.
How do you think this situation has changed since you wrote Gamer Theory?
MW: Well, to me it looks like the tendency analyzed in Gamer Theory became even more the case. GamerGate looks among other things like a reactive movement among people who really want the neoliberal utopia in all its actual neofascist and misogynist glory to not be exposed as different to everyday life. When women gamers or game journalists stick their hands up and say, “hey, wait a minute”1, they just want to mow them down with their pixelated weapons. So the paradox is that as gamespace becomes more and more ubiquitous, the tension between promise and execution becomes ever more obvious.


F: Do you see the term Gamification that many theorists use currently as an elaboration of the ideas you developed in Gamer Theory? Or are there significant new ideas being explored?
MW: Ha! Well no, gamification was about celebrating the becoming game-like of everyday life. So I always saw that as a kind of regression from thinking about the phenomena to sort of cheerleading for it.
F: The software developer and software freedom activist Richard Stallman, when visiting Korea in June 2000 illustrated the meaning of the word ‘Hacker’ in a fun way. During a lunch with GNU fans a waitress placed 6 chopsticks in front of him. Of course he knew they were meant for three people but he found it amusing to find another way to use them. Stallman managed to use three in his right hand and then successfully pick up a piece of food placing it into in his mouth. Stallman’s story is a playful illustration of “hack value,” about changing the purpose of something and making it do something different to what it was originally designed to do, or changing the default.2
Stallman was highlighting fun and the mischievous imagination as part of the spirit of what he sees as hack value.
Where do you see lies the hack value in games culture? What has happened to the fun in games? Who’s having it and where is it happening?
MW: Stallman is one of the greats. Sometimes, people have this experience of scientific or technical culture as one of free collaboration, where there’s a real play of rivalry and recognition but based on producing and sharing knowledge as a kind of gift. JD Bernal had that experience in physics in the 30s and Stallman had, I think, a similar experience in computing. I think it’s important for those of us from the arts or humanities to honor that utopian and activist impulse coming out of more technical fields.

There’s a lively, critical and even avant-garde movement in games right now. That’s part of why it has provoked such a fierce reaction from a certain conservative corner. The culture wars are being fought out via games, which is as it should be, as it’s one of the dominant media forms of our times. So there’s certainly some sophisticated fun to be had alongside the more visceral pleasure of clearing levels.
F: “Our species’ whole recorded history has taken place in the geological period called the Holocene – the brief interval stretching back 10,000 years. But our collective actions have brought us into uncharted territory. A growing number of scientists think we’ve entered a new geological epoch.”3 And, this new geological epoch has been proposed as – the Anthropocene.
In your essay ‘Critical Theory After the Anthropocene’4 you say “At a minimum, the Anthropocene calls on critical theory to entirely rethink its received ideas, its habituated traditions, its claims to authority. It needs to look back in its own archive for more useful critical tools.”
What are these ‘useful critical tools’ and how might theorists, new media artists, game designers and society at large put these to work?
MW: The ‘cene’ part of Anthropocene (from the Greek kainos) means a qualitative break in time. If time is in a sense always different, then kainos is the differently-different – a new kind of time. Those like Paul Crutzen who have advocated the use of the term Anthropocene to designate a new geological time have issued a major challenge as to how to interpret such a possibility. I leave it to the scientists to figure out if such a claim is scientifically valid. As someone trained in the humanities, I think the generous, comradely, cooperative thing to do is to try to interpret what our friends and colleagues in the sciences are telling us about the times. So in Molecular Red that was what I set out to do. Let’s take seriously the claim that these times are not ‘like’ other times. That I think calls for a rethinking of what from the cultural past might be useful now. I think we need new ancestors. Which is why, in Molecular Red, I went looking for them, based on the question: to which past comrades would the Anthropocene come as no surprise? I think Alexander Bogdanov, who understood a bit about the biosphere and the carbon cycle, would not be surprised. I think Andrey Platonov, who wrote about the attempts and failures to build a new kind of infrastructure for the Soviet experiment in a new mode of production would not be surprised. There are others, but those I thought were particularly helpful, not least because their Marxism remained in dialog with the sciences and technical arts. I don’t think the more romantic anti-science side of Western Marxism and continental thought is all that helpful at the moment, not least because it rules out of court exactly the kinds of scientific knowledges through which we know about the Anthropocene in the first place. The anti-science critique has been captured by the right, so we need new tactics.
F: Who’d be empowered by an encounter with your ideas and where do you see the potential for agency in the current economic and environmental contexts?
MW: Not for me to say really. Writers are usually the last people to have any clues as to what their writing says. There’s a sort of idiot quality to banging away on a keyboard. We’re word processors. Its always surprising to me the range of people who find something in what I write.
My hunch is that the future is in the hands of an alliance between those who make the forms and those who make the content: a hacker and worker alliance. It is clear that this civilization has already become unreal. Everyone knows it. We have to experiment now with what new forms might be.
F: And, where in the world do you see examples of individuals, groups and organizations, and or companies – who are putting into action some of the critical questions that you’re exploring in your writing?
MW: Besides Furtherfield? I never like to give examples. Everyone should be their own example. To détourn an old slogan of the 60s: be impossible, do the realistic!
F: In your later essay ‘The Drone of Minerva’5 you continue to write about the Anthropocene. But, you also bring to the table the subject of the Proletkult.6 The Proletkult aspired to radically modify existing artistic forms of revolutionary working class aesthetic which drew its inspiration from the construction of modern industrial society in Russia. At its peak in 1920, Proletkult had 84,000 members actively enrolled in about 300 local studios, clubs, and factory groups, with an additional 500,000 members participating in its activities on a more casual basis.
You are writing about the Proletkult in your latest book. Could you tell us a little something about this and how it will connect to contemporary lives?
MW: Proletkult was influential in Britain too, during the syndicalist phase of the British labor movement, up until the defeat of the 1926 general strike. After that the dominant forms were, on the one hand, the ethical-socialism and parliamentary path of the Labour Party, or the revolutionary Leninist party. Well, those paths have been defeated now too. I think we have to look at all of the past successes and failures all over again and cobble together new organizational and cultural forms, including a 21st century Proletkult.7 What that might mean is trying to self-organize in a comradely way to try and gain some collective charge of our everyday lives. It does not mean just celebrating actually existing working class cultures. Rather it’s more about starting there and developing culture and organization not as something reactive and marginalized but as something with organizational consistency and breadth. Since the ruling class clearly doesn’t give a fuck about us, let’s take charge of our own lives – together.
Thank you McKenzie Wark – Ruth Catlow & Marc Garrett 😉
Ruth Catlow will be at Transmediale 2015 CAPTURE ALL, moderating the keynote Capture All_Play with McKenzie Wark, on Sat, 31 Jan at 18:00.
Ruth is also participating in two other events, Play as a Commons: Practical Utopias & P2P Futures and The Post-Digital Review: Cultural Commons – http://www.transmediale.de/content/ruth-catlow
Die GstettenSaga: The Rise of Echsenfriedl review. SPOILER WARNING!
Johannes Grenzfurthner’s Post-Apocalyptic DIY Epic on Makers, Hacktivism and Media Culture.
“A mad post-collapse satire of information culture and tech fetishism, in a weird sort of melding of Stalker, Network, and The Bed-Sitting Room.” (Richard Kadrey)
Die GstettenSaga: The Rise of Echsenfriedl is an Austrian hackploitation art house film by Johannes Grenzfurthner, mastermind of the international art-technology-philosophy group monochrom, co-produced by the media collective Traum & Wahnsinn. Reimagining the makerspace as grindhouse, the story is set in the post-apocalyptic aftermath of the “Google Wars” – an armed global conflict between the last two remaining superpowers China and Google – which has turned what remained of the Alps into a Gstetten.
In Austrian German, “Gstetten” translates to wasteland, outback or ‘fourth world’ (Manuel Castells) and is a popular name for provincial towns – and sometimes just the less sophisticated parts of them. The area’s biggest semi-urban sprawl is Mega City Schwechat, the former home of Vienna International Airport, a refinery and a beer brewery. It is governed by the evil media mogul Thurnher von Pjölk (Martin Auer), a pretender who claims to be the inventor of key publishing technologies such as letterpress printing and rules the area with his tabloid newspaper. But the hegemony of his yellow press empire is contested by – spoiler alert! – makers, hackers and nerds, who are more leaning towards electronic media such as the recently rediscovered television. In order to get rid off this bothersome opposition, Pjölk devises an evil plan for wiping out Schwechat’s insubordinate creative class.

In an insidious political move, he pretends to reach out for the technophile faction by commissioning two of his reporters, the bootlicking opportunist Fratt Aigner (Lukas Tagwerker) and the brainy geek girl Alalia Grundschober (Sophia Grabner), to conduct an exclusive TV interview with the ultimate Gstetterati icon, the legendary innovator Echsenfriedl (“Lizard Freddy”) – on the basis of precarious employment conditions. The title character, who turns out to be an basilisk, embodies a mix of Steve Jobs, Richard Stallman and Julian Assange and lives in the depths of Niederpröll in his hideout much like Subcomandante Marcos – partly in order to protect the world from his killing gaze, which would, audio-visually transmitted, turn the whole of his fan base immediately to stone.
Grenzfurthner’s sci-fi-horror adaption of the Divine Comedy takes us on a retro-futuristic post-cyberpunk adventure in the tradition of cinema grotesque back to the dark days which preceded the Internet. The journey of our heroes – distinctively resembling Tarkovsky’s ‘stalkers’ – is a quest for extinct media technologies but their search for Echsenfriedl eventually leads the two protagonists to a deepened understanding of who they really are: the media industry’s precarious workforce under spectacular capitalism. While Fratt’s dirt track to enlightenment is paved with stumbling blocks, his brainy Beatrice advances with the determination of a Harawayian cyborg who makes use of her superior technical skills to save them from the zombified folk populating the Gstetten: uncanny creatures from the Kafkaesque bestiarium of Austria’s undead bureaucracy and its hanger-ons like armed-to-the-teeth Postal Service subcontractors (brilliant: monochrom’s Evelyn Fürlinger, also Grenzfurthner’s ex-wife) or the once powerful Farmers Association led by Jeff Ricketts (Firefly, Buffy the Vampire Slayer), who are worshipping antique pre-war EU funding applications as their sacred scriptures. Our friends receive the final hints for their search from the Sphinx Philine-Codec Comtesse de Cybersdorf (Eva-Christina Binder), a fantasy femme fatale who is torn between Plöjlk and Echsenfriedl, and the bearded drag queen Heinz Rand of Raiká (David Dempsey), an eccentric agricultural cooperative banker and possible descendant of Conchita Wurst.

The Gstettensaga’s fascinating cinematic pastiche is more than just a firework of rhizomatic intertextuality, a symptom of the depthlessness of postmodern aesthetics or excessive enthusiasm for experimentation in the field of form. In their infamous 1972 book Anti-Oedipus, Gilles Deleuze and Félix Guattari have identified the technique of bricolage as the characteristic mode of production under “schizophrenic” capitalism, a facet triumphantly magnified by the filmmakers. If every discourse is bricoleur, like Jacques Derrida suggested, suddenly ‘context’ can become the artist’s material or even a form of art in its own right:
“The more artists are consigned to an existence within a patchwork of niches, the more dependent they become on information resources, communication and networking. In this respect, aesthetic artefacts must take a stance toward a plethora or markedly heterogeneous contexts that sediment in one way or another: the conditions and circumstances surrounding their production, their various social fields from which (and for or against which) they speak: real or imagined audiences toward (or against) whose values a work, an approach or a position is targeted. This play with the factors affecting it and among which it must mediate has become an essential trait on an art form that might best be described as ‘Contextualism’.” [1]

What I found especially intriguing about the Gstettensaga is how the filmmakers responded to the various challenges of the feature film format by contextualising the whole production process, distribution, language adaptions (subtitles are an integral part of the story), soundtrack and even the viewing experience.
The film was initially commissioned by Austrian public broadcasting station ORF III as part of the series Artist-in-Residence for a budget of only €5000, set to be produced within a six months period. In response, monochrom used an embedded prank to raise money. The movie contains a text insert similar to watermarks used in festival viewing copies, which asks the viewer to report the film as copyright infringement by calling a premium-rate phone number (1.09 EUR/minute) and enabled Grenzfurthner to co-finance the film with proceeds from this new strategy he has named ‘crowdratting’. [2]
The Contextualist script – including outlines of scenes for improvisation – was written by Grenzfurthner and Roland Gratzer in just a couple of days in November 2013 in a Viennese restaurant. They also incorporated ideas that came up during their weekly meeting with the entire production crew, whereas some of the backstory was first created for monochrom’s pen-and-paper role-playing theatre performance Campaign. Principal photography – the camera work of Thomas Weilguny deserves the highest praise – commenced on December 2, 2013 and ended January 19, 2014, which left nearly 5 weeks for post-production and editing. Due to the fast production process and the financial limitations, no film score was composed for the Gstettensaga – instead, Grenzfurthner used an assortment of 8bit, synth pop and electronica tracks especially for their specific retro quality because “they may sound old-school to us, but not in the world of the Gstettensaga, where all retro electronic music is still impossible and futuristic.” [3]
The retro-futuristic world of Echsenfriedl is coming to a film festival, hacker con or Pirate Bay near you.
http://www.monochrom.at/gstettensaga/
Tamtam (Seara de proiectie la TT) / May 7, 2014 (Timisoara, Romania)
KOMM.ST Festival / May 11, 2014 (Anger, Austria)
Supermarkt (Dismalware) / June 7, 2014 (Berlin, Germany)
Fusion Festival / June 25-29, 2014 (Lärz Airfield, Mecklenburg, Germany)
Roswell International Sci Fi Film Festival / June 26-29, 2014 (Roswell, NM, USA)
iRRland movie night / June 30, 2014 (Munich, Germany)
qujochö Film Summer / July 3, 2014 (Linz, Austria)
HOPE X / July 18-20, 2014 (New York, New York, USA)
Fright Night Film Fest / August 1-3, 2014 (Louisville, KY, USA)
Gen Con Indy Film Festival 2014 / August 14-17, 2014 (Indianapolis, Indiana, USA)
San Francisco Global Movie Fest / August 15-17, 2014 (San Jose, CA, USA)
Rostfest / August 21-24, 2014 (Eisenerz, Austria)
Noisebridge / August 29, 2014 (San Francisco, USA)
/slash Filmfestival / September 18-28, 2014 (Vienna, Austria)
Simultan Fest / October 6-11, 2014 (Timisoara, Romania)
Phuture Fest / October 11, 2014 (Denver, Colorado, USA)
prol.kino / October 14, 2014 (Graz, Austria)
In “How Readers Will Discover Books In Future“, science fiction author Charles Stross envisions a future in which weaponized eBooks demand your attention by copying themselves onto your mobile devices, wiping out the competition, and locking up the user interface until you’ve read them.
This is only just science fiction. Even the earliest viruses often displayed messages and malware that denies access to your data until you pay to decrypt it already exist. ePub ebooks can execute arbitrary JavaScript, and PDF documents can execute arbitrary shell scripts. Compromised PDFs have been found in the wild. Stross’s weaponized ebooks are not more than one step ahead of this.
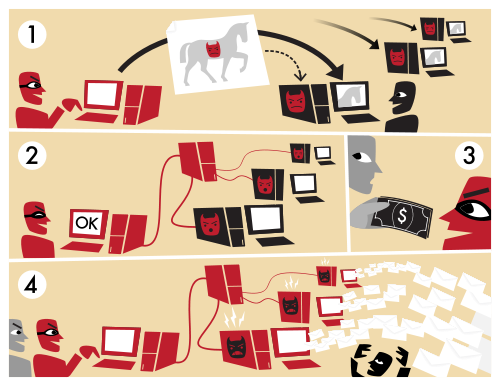
Why would eBooks want to act like that? To find readers. In the attention economy, the time required to read a book is a scarce resource. Most authors write because they want to be read and to find an audience. Stross’s proposal is just an extreme way of achieving this. In Stross’s scenario, authors are like the criminal gangs that use botnet malware to get your computer to pursue their ends rather than your own, use adware to coerce you into performing actions that you wouldn’t otherwise, or use phishing attacks to get scarce resources such as passwords or money from users.
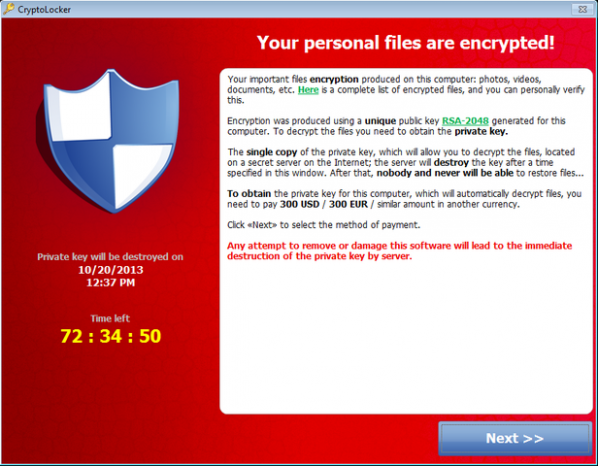
As so much new art is made that even omnivorous promotional blogs like Contemporary Art Daily cannot keep up, scarcity of attention becomes a problem for art as well as for literature. And when people do visit shows they spend more time reading the placards than looking at the art. In these circumstances Stross’s strategies make sense for art as well. Particularly for net art and software art.
A net or software artwork that acted like Stross’s vampire eBooks would copy itself onto your system and refuse to unlock it until you have had time to fully experience it or have clicked all the way through it. It could do this in web browsers or virtual worlds as a scripting attack, on mobile devices as a malicious app, or on desktop systems as a classical virus.
Unique physical art also needs viewers. Malicious software can promote art, taking the place of private view invitation cards. Starting with mere botnet spam that advertises private views, more advanced attacks can refuse to unlock your mobile device until you post a picture of yourself at the show on Facebook (identifying this using machine vision and image classification algorithms), check in to the show on FourSquare, or give it a five star review along with a write-up that indicates that you have actually seen it. In the gallery, compromised Google Glass headsets or mobile phone handsets can make sure the audience know which artwork wants to be looked at by blocking out others or painting large arrows over them pointing in the right direction.

Net art can intrude more subtly into people’s experiences as aesthetic intervention agents. Adware can display art rather than commercials. Add-Art is a benevolent precursor to this. Email viruses and malicious browser extensions can intervene in the aesthetics of other media. They can turn text into Mezangelle, or glitch or otherwise transform images into a given style. In the early 1990s I wrote a PostScript virus that could (theoretically) copy itself onto printers and creatively corrupt vector art, but fortunately I didn’t have access to the Word BASIC manuals I needed to write a virus that would have deleted the word “postmodernism” from any documents it copied itself to.

Going further, network attacks themselves can be art. Art malware botnets can use properties of network topography and timing to construct artworks from the net and activity on it. There is a precursor to this in Etoy’s ToyWar (1999), or EDT’s “SWARM” (1998), a distributed denial of service (DDOS) attack presented as an artwork at Ars Electronica. My “sendvalues” (2011) is a network testing tool that could be misused, LOIC-style, to perform DDOS attacks that construct waves, shapes and bitmaps out of synchronized floods of network traffic. This kind of attack would attract and direct attention as art at Internet scale.

None of this would touch the art market directly. But a descendant of Caleb Larsen’s “A Tool To Deceive And Slaughter” (2012) that chooses a purchasor from known art dealers or returns itself to art auction houses then forces them to buy it using the techniques described above rather than offering itself for sale on eBay would be both a direct implementation of Stross’s ideas in the form of a unique physical artwork and something that would exist in direct relation to the artworld.
Using the art market itself rather than the Internet as the network to exploit makes for even more powerful art malware exploits. Aesthetic analytics of the kind practiced by Lev Manovich and already used to guide investment by Mutual Art can be combined with the techniques of stock market High Frequency Trading (HFT) to create new forms by intervening in and manipulating prices directly art sales and auctions. As with HFT, the activity of the software used to do this can create aesthetic forms within market activity itself, like those found by nanex. This can be used to build and destroy artistic reputations, to create aesthetic trends within the market, and to create art movements and canons. Saatchi automated. The aesthetics of this activity can then be sold back into the market as art in itself, creating further patterns.
The techniques suggested here are at the very least illegal and immoral, so it goes without saying that you shouldn’t attempt to implement any of them. But they are useful as unrealized artworks for guiding thought experiments. They are useful for reflecting on the challenges that art in and outside the artworld faces in the age of the attention-starved population of the pervasive Internet and of media and markets increasingly determined by algorithms. And they are a means of at least thinking through an ethic rather than just an aesthetic of market critique in digital art.
The text of this article is licenced under the Creative Commons BY-SA 4.0 Licence.
Featured image: Sam Meech, Punchcard Economy, 2013. Photo courtesy of FACT.
The new exhibition “Time & Motion” at FACT in Liverpool, UK, takes the pulse of punchcard protocol and creative capital in our own “Modern Times”.
The exhibition Time & Motion: Redefining Working Life at FACT Liverpool is a collaboration between FACT and the Creative Exchange at the Royal College of Art – an initiative which looks at how arts and humanities researchers can work with industry to effect digital innovation. Rachel Falconer reviews the exhibition in the context of the paradoxical dynamics of cognitive capital and the changing landscape of the labour market.
Now self-employed,
Concerned (but powerless),
An empowered and informed member of society
(Pragmatism not idealism),
Will not cry in public,
Less chance of illness,
Tires that grip in the wet
(Shot of baby strapped in back seat),
A good memory,
Still cries at a good film,
Still kisses with saliva,
No longer empty and frantic like a cat tied to a stick,
That’s driven into frozen winter shit
(The ability to laugh at weakness),
Calm,
Fitter,
Healthier and more productive
A pig in a cage on antibiotics.
Fitter Happier, Radiohead.
The frantic quest for the elusive Shangri-La of work/life balance is a neurotic luxury afforded only to the always-on, hyper-connected generation of precariously unstable home office workers[1] in our hypercapitalist society. The working rhythms of this emergent class of “precariat” [2] are far removed from the forensically prescribed scientific management resulting from the time and motion studies associated with Taylorism at the beginning of the last century. This shift in working patterns generated by the digital revolution is the primary focus of the exhibition Time and Motion, Redefining Working Life currently at FACT, Liverpool. From an archival, filmic view of the automated, (Western) industrial factory labourer to contemporary portraits of the global information worker’s state of perpetual imbalance and non-stop, hyper-connectedness [3] the participating artists expose the – often contradictory – ecologies of labour, consumption, and the conditions in which they operate. The exhibition also marks the collaboration between FACT and Creative Exchange at the Royal College of Art – an initiative which looks at how arts and humanities researchers can work with industry to effect digital innovation and confront contemporary modes of production.
Taking the archival stimulus of time and motion measurement as its title and industrial work patterns as a starting point, the exhibition Time & Motion is the latest in a series of exhibitions and symposia addressing immaterial labour and new working patterns in the age of globalisation and creative capital.[4] Rather than following the well-trodden path of casting the figure of the artist as digital labourer, or attempting to portray an expansive, post-colonial view of nomadic, labouring diasporas, Time and Motion reflects a more subversive and fragmented approach to the politics of work, rest and play in the global information economy.
Sam Meech’s Punchcard Economy is at once a homage to the textile industry and a recognition of the contemporary precariat. With more than a symbolic nod to northern England’s textile heritage, Punchcard Economy consists of a machine-knitted reinterpretation of the Robert Owen’s 8-8-8 ideal work/life balance.[5] The piece was produced on a domestic knitting machine using a combination of digital imaging tools and traditional punchcard systems. During a residency at FACT last year, Meech collected punchcards from visitors detailing their working hours. This data was then translated into a knitting pattern which was used to generate the final work – a banner depicting the contemporary working day. Any hours worked outside the eight-hour day appear as a glitch within the fabric. This banner – historically a symbol of the working class and trade unions – also denotes the fragmentation and blurring of national class structures in the era of globalisation.
The move towards a flexible, open labour market has not eroded the class system completely, but a more fragmented global class struggle has emerged. The “working class”, “workers”, “proletariat” are terms that have been embedded in our (Western) culture for centuries, and used as badges of honour by some, and terms of derision by others. By incorporating a large cross-section of working society under one banner, Meech has literally – in stitching different socio-economic groups together into the very fabric of the working day – rendered the once potent archaic class signifiers as little more than evocative labels.[6]

“75 Watt” by artist Cohen Van Balen and choreographer Alexander Whitley also riffs on the trope of the long fought for 8 hour working day. Deriving its title from a quote from Marks’ Standard Handbook for Mechanical Engineers: “A labourer over the course of an 8-hour day can sustain an average output of about 75 watts”, the film is a subversive ballet of the complex and often skewed relationships between production, consumption and distribution in the post-industrial age. The film features a group of Chinese labourers working an assembly line, (playing on the stereotypical “Made in China” trope). The object they produce, however, has no logical use. The purpose of the exercise is simply to choreograph the combined movements performed by the labourers in the manufacturing process. The work examines the nature of mass-manufacturing on differnt levels; from the geo-political context of hyper-fragmented labour to the bio-political condition of the human body on the assembly line. Echoing the Taylorist ideal, here we see engineering logic taken to its conceptual extreme; through the scientific management of every single movement we witness the passage of factory labourer to a man-machine.
By shifting the purpose of the labourer’s actions from the efficient production of objects to the performance of choreographed acts, mechanical movement is reinterpreted into dance. The artists ask: “What is the value of this artefact that only exists to support the performance of its own creation? And as the product dictates the movement, does it become the subject, rendering the worker the object”?
This operatic construction line also points towards the ultimate failure of scientific management. Taylorism was always dictated by the needs of capitalist exploitation, but in its pure form it proved to be inefficient in drawing on workers’ talent and potential. In time the bourgeoisie recognised the inadequacies in Taylorism, and Taylorist methodology was mostly withdrawn by the 1930s. However, this was not the end of time and motion measurement. More recent management theories include Theory X and Theory Y introduced by Douglas McGregor in the 1960s.[7] Contemporary Taylorism takes the form of the Lean practices introduced into major departments of the British civil service (including HMRC, DWP, MOJ, and MOD). Workers incorporate “efficiency savings” as an integral part of their job, and work priorities are monitored by the soft panoptic gaze of non-hierarchical “collaborative practice”. Here,workers time their work processes, identify forms of waste, and propose changes in work practices. This “bottom-up” approach goes hand in hand with the new language of management – as managers morph into “leaders”. As efficiency savings are made from workers’ suggestions, the “leaders” try to enforce impossible targets, and decide whose post is next to be eliminated – hence the creation of the precariat. As part of the precariousness of employment, workers not only worry about losing their jobs, but also have to propose measures which, in the name of efficiency, might put them out of work. Added to this the increasing automation of work and the burgeoning AI scene, where does human cognition stand in all of this?

Inari Wishiki’s set of ludicrious alternative employment models (such as Banana Multiplier), are in reminiscent of the subversive, performative models of the Fluxus movement. Inari’s online work Recruit Agency for People Who Don’t Want To Work dramatizes this staging of an alternative labour market. The website includes documentation of a series of performances by the artist exploring the premise that with the proliferation and development of technology, we as humans have lost our place in the world of work, and yet still need to appear to be “useful” in order to earn a living.
Recruit Agency For People Who Don’t Want To Work is a set of systems which allow people to engage in the act of commerce while abandoning “all the meaningless rituals of having to be useful in order to earn money”. In INARI TRADING CARD, the artist documents the way in which “essential” workers function as a social infrastructure. He observes that “money was naturally following those workers according to their essential motions, unlike that of workers who seek after money”. These set of performances are an ironic counterpoint to the hyper-efficiency promoted by neo-Taylorism, and point towards the informal norms that are in tension with the industrial time norms still permeating social analysis, legislation and policymaking in the globalization era.
In his text “The Value of Time Spent” in the accompanying catalogue to the exhibition, Mike Stubbs supports this strategy of “design for disassembly” and novel values of exchange. Stubbs maintains that these alternative ecologies of exchange are necessary in order to allow us to question how we spend our time, and for us to lay bare the new patterns of professional fulfilment and social relations inherent to our hyper-mediated society.

The classic distinction between the workplace and the home was forged in the industrial age, and when today’s labour market regulations, labour law and social security systems were constructed, the norm was a fixed workplace. This model has now fragmented and crumbled and the term social factory, popularized by Tiziana Terranova and others, is applied to describe this shift “from a society where production takes place predominantly in the closed site of the factory to one where it is the whole of society that it is turned into a factory – a productive site”.[8] The production is one of value, where the collective efforts of intelligence and creativity are networked, controlled and exploited. Labour takes place everywhere, and the discipline or control over labour is universally exercised. But policies are still based on a presumption that it makes sense to draw sharp distinctions between the workplace and home – and between workplace and public space. In a tertiary market society, this model is obsolete, leaving the information worker increasingly pressurized and isolated.

One of the recurring themes in Time & Motion is this hybrid and compromised locus and infrastructure of the work place. Harun Faroki’s moving image work A New Product presents an insider’s view of the paradoxical construction of so called “fluid” working environments. He describes his new film as: “Scenes from meetings within a company which advises corporations how to design their offices — and the work done there. The film shows that words are not just tools, they have become an object of speculation.” In this work, he stages the brainstorming sessions of a business consultancy specialising in the design of workspaces, offices and new concepts for mobile work hubs. The resulting seductive imagery of the ideal workspace is an exercise in brand development pastiche rendered as pseudo video game.

Time & Motion also stages a co-working space, developed by the RCA CX team, which weaves together venue, audience, workspace and digital space – presenting the entrance space of the gallery space into a live research ‘lab’. Visitors are encouraged to participate in the research, interaction and interventions, and workshops, salon discussions, and hacking and making sessions are woven into the experimental fabric of the exhibition.
The ‘CX Co-Working Space’ features three design interventions. The first, Hybrid Lives, features video work by Karen Ingham and an interactive installation responding to data traffic, dressed with ‘co-working furniture’. Where Do You Go To? is a wall-mounted moving freize showing the output from an app, co-designed with a group from the BBC, with the mission to connect remote workers through exchanging, Snap-chat-like (pre-hack) images of desks and workspaces. According to Ben Dalton, one of the main developers, this sharing of ‘desk context’ helps form a synergy of ‘headspace’ between remote workers.



Taking its cue from Frances Cairncross’s 1995 “The Death of Distance”, where the compelling vision that, over time, the communications revolution would release us from geographic locations, the project illustrates how digital space has redefined our working lives. However, for all its good intentions, this gesture towards remote solidarity seems to be muddying the new principles and rhythms of work with Taylorist and later Fordist ideals of panoptic surveillance and somehow stands in direct opposition to the emancipatory rhetoric of convergence culture.
Time and Motion focuses primarily on a particular demographic of labourer (generally the global information worker), and paints the picture of a tertiary lifestyle which involves multitasking without control over a narrative of time use, and habitual fractured thinking – where non-stop interactivity (a digital version of Taylorist motion) is crack cocaine for the drones. For this category of workers, the workplace is everyplace – diffuse, unfamiliar, a zone of insecurity. We are left with a “thin democracy” in which people are disengaged from political activity except when jolted into consciousness by a shocking event or celebrity meltdown witnessed virally on Youtube during office hours. As more work and labour takes place outside the pre-determined workplace – in the hybrid environments of cafes, trains and across the domestic landscape – the very idea of a work/life balance seems like an alien ideal to aspire to.In an open tertiary society, the industrial model of time, and the bureaucratic time management of factories and office blocks, breaks down. There is no stable time structure and we are increasingly losing our grip on our own time. Time and Motion at FACT interrogates the impact of this fragmentation on the aesthetic forms of contemporary art, and contemplates how artists might offer a critique of our neo-Taylorist predicament.
Read and learn how to solve a Rubiks Cube with the layer-by-layer method. It can be learned in an hour.
Richard Stallman[1] the outspoken promoter for the Free Software movement, hates Facebook with a passion. He proposes that we should all leave Facebook and either find or build our own alternatives. The evidence offered by Stallman’s and the Electronic Frontier Foundation’s (EFF), who have been fighting for Internet freedoms since the 90s [2] shows how necessary it is that we understand and are more pro-active in managing the personal data that we give away through our online activities.
When we subscribe to Web 2.0 platforms such as Facebook we are at the mercy of the data brokers. These companies trade in people’s personal data; information which is aggregated by monitoring user actions and interactions across social media. This information can include “names, addresses, phone numbers, details of shopping habits, and personal data such as whether someone owns cats or is divorced.”[3] Fast moving developments in social media, make it difficult to keep up with the effects and consequences of these platforms. This is why the work of groups such as Commodify Inc. is so valuable. They bring imaginative and critical attention to the situation, sharing their knowledge of these daily networked complexities and correcting what they see as its negative effects.
Commodify Inc. is an artist-run Internet startup producing projects to help individuals capitalize on their online monetary potential. Their intention is to correct the imbalance of power in markets where users have no control over the transactions made with their personal data. They have completed various artistic projects and interventions on social media like, Fame Game, Give Me My Data, and Web 2.0 Suicide Machine. The co-founders are Birgit Bachler, Walter Langelaar, Owen Mundy, Tim Schwartz, with additional contributors Joelle Dietrick and Steven Alvarado.
Their new project Commodify.Us, was initiated when Owen Mundy and Tim Schwartz were invited by moddr_ to a residency in their lab in the summer of 2012 – when they were still a part of the WORM collective in Rotterdam. They worked on an initial idea that would succeed previous experiences of their already well-known and respected projects.
Commodify.Us is currently in beta phase. It promises to provide a platform for people to regain control over the commercial exploitation of their own personal data.
Intrigued by this project I contacted one of the co-founders, Walter Langelaar via email and asked him a few questions about this new platform.
Marc Garrett: Commodify.Us is for people to have greater control over their data. And it works when users export their data from social media websites and upload it to your platform. How will these users gain more control over their data and why is this important?
Walter Langelaar: Commodify.Us provides a platform for you to regain control over the commercial exploitation of your personal data. After exporting your profile data from social media websites and uploading the data to Commodify.Us, you can directly get in contact with interested buyers. On the importance for users I would say that it’s part raising awareness surrounding the monetization of profile data, and part creating a platform where people might work out and discuss how to do this themselves.
MG: It proposes to re-imagine the potential of relational data, creating a casting agency for virtual personas. I’m wondering what this may look like?
WL: We were too. In an early stage of the project we played with the idea that peoples’ various profiles could function like that within an agency; a client would ask for a specific set of qualities and/or characteristics within a set of profiles, and we could provide for this based on the uploads and their licensing options as set by the user. In the end we abandoned this idea for clarity.
MG: Commodify.Us offers people the opportunity to be part of an economy where interested buyers will pay to use the data supplied, unlike existing social media websites. How does this work?
WL: We are gearing up for a launch where the main goal will be to get a critical mass of around, a 1000 profiles. We anticipate that only with this kind of mass or volume will our initiative take hold with the potential buyers we have in mind, and the same goes for the more creative projects that could use the (open) data. Regarding the open profile data and otherwise licensed profiles that allow for reuse, we are researching the idea of ‘Fair Data’ (as in Fair Trade) and how to implement this as a profitable protocol for the end-user.

“Net activists construct tools whose intervention potential can be initiated by users under net conditions. These tools enable activists to develop new strategies in the data space of the Internet because they offer new means: New means afford new ends.”[4] (Dreher)
In his publication Networks Without a Cause: A Critique of Social Media, Geert Lovink lays down the gauntlet and asks us to “collectively unleash our critical capacities to influence technology design and workspaces, otherwise we will disappear into the cloud.” Anna Munster opens her excellent survey, Data Undermining: The Work of Networked Art in an Age of Imperceptibility, by saying “The more data multiplies both quantitatively and qualitatively, the more it requires something more than just visualisation. It also needs to be managed, regulated and interpreted into patterns that are comprehensible to humans.”[5] Commodify.Us goes one step further by allowing users to manage, regulate, repattern and reappropriate their own data using tools that share an essential functionality (if not purpose) with the power tools of Web 2.0.
Those previously seen as rebellious hacktivists are moving into new territories that deal with concepts of service. There has been a significant rise of artists exploring technology to influence mass Internet activity, against the domination of corporations who are data mining and tracking our on-line activities. Another example is TrackMeNot developed by Daniel Howe and Helen Nissenbaum. This is an extension created for the Firefox browser. “It hides users’ actual search trails in a cloud of ‘ghost’ queries, significantly increasing the difficulty of aggregating such data into accurate or identifying user profiles.”[6]
Howe and Nissenbaum mention they are aware their venture is not an immediate solution. However, the more we hear of and join these imaginative strategies “whereby individuals resist surveillance by taking advantage of blind spots inherent in large-scale systems” [7], and the more we adapt our behaviours to adopt these new ‘activist’ services, the more we demonstrate the demand for these new alternatives. And by so doing, we argue for the value of services that we can trust not to steal or manipulate our social contexts for financial and political gain.

A significant value offered by the Commodify.Us platform is the power to manage our own data. The simple act of downloading our own data from Facebook, and then uploading it to Commodify.Us supports us to rethink what all this information is. What once was just abstract data suddenly becomes material that we can manipulate. Alongside this realization arrives the understanding that this material was made by our interactions with all these platforms, and that other people are spying on us and making money out of it all. Once this data material is uploaded onto the Commodify.Us platform, it asks if we want this stuff to be a product under our own terms, or if we wish to make art out of it using their tools.
This is a cultural shift that demonstrates how contemporary Hacktivists are developing software that promises to offer realistic service infrastrucutures. When I interviewed Charlie Gere in 2012[8] he said that these artists “are not part of the restricted economy of exchange, profit, and return that is at the heart of capitalism, and to which everything else ends up being subordinated and subsumed. Thus they find an enclave away from total subsumption not outside of the market, but at its technical core.” For me, this kind of work is of central importance to the contemporary era, and it only occurs where artists cross over into territories where their knowledge of networks directly contributes to the building of alternative structures of social independence.
Featured image: Urinal, 2011, 3D printable digital model. Model by Chris Webber, commissioned by Rhea Myers
Rhea Myers is an artist and programmer and keen advocate of the Open Source Software culture and community. Much of the work he creates and the ideas he explores are rooted in sharing; making works that are available for others to use in their own way. This concept can be something of a paradigm shift for a traditional art world – where the notion of an artist as someone visited by the muse and given divine insight into some aspect of the world around us reigns supreme. We imagine said artist sharing their visions through one-off artefacts that become valuable in the competitive marketplace of the consumerist commercial art world.
The Shareable Readymades project works within the realms of Net art, but Shareable Readymades are output as a real-world object. Using a downloadable, freely licensed 3D model of the art work, Shareable Readymades can be printed using modern 3D printing technology wherever the equipment is available. The code for creating the 3D models is available on several websites including Rhea Myers’ own Github account. The artefacts are scalable, which gives the option of deciding what size – up to that of the original item – they print at.
Beyond the idea of a ready-made artefact is the thought, lingering in the air between creation and conception in this work, of the digital blueprint for it: the Blender file (Blender is the 3D software used to model the work). Given the digital and mechanical process involved in creating the work and the tightly wound connection between them, it might seem difficult to know where in the process the work actually comes into existence? Perhaps it is easier to think of the entire process as being the product itself. With 3D printing another possibility emerges: that 3D printing isn’t the total artefact in itself. In industrial design, pieces are created to give real form to objects and allow designers to have a tangible example of what they are trying to develop. They become a step in the production and act as a conceptual point in a longer process. Rhea Myers’ Shareable Readymade Urinals are close to the conceptual nature of Duchamp’s ‘readymades’ – specifically Fountain – because they will never become functioning objects. In our understanding, they increasingly come to represent ethereal objects removed from function, or a discussion about the increasingly fuzzy line between everyday objects and objects defined as ‘art’.
There’s a process of induction into ‘being’ involved and part of this is the commissioning. Myers commissioned the 3D models from Christopher Webber and then made them publicly available for download so that anyone can own an original piece of art.
In Abstract Hacktivism, Otto Von Busch and Karl Palmas lay out an argument for reconfiguring the way we think about the world around us. Tracing a path from Michel Serres through to Manuel DeLanda, they argue that new developments in technology change the language and by corollary, the way we frame our thoughts about the world. As DeLanda has said:
“He [Serres] sees in the emergence of the steam motor as a complete break with the conceptual models of the past. […] When the abstract had been dissociated from its physical contraption [the actual motor] it entered the lineages of other technologies, including the “conceptual technology” of science.”[1]
The essays in this all-too-short book end with the personal computer and how we think about society in terms of hardware. The authors only briefly touch on the emergence of software as a means for constructing metaphors for contemporary life, and Rhea Myers’ ‘readymades’ take this even further, encountering the idea of production.
The digital production and mechanical output perfectly summarise so much about life in the 21st Century. Our understanding of consumerism itself is gradually changing thanks to the growth of Internet shopping. We select our produce from a database of text and imagery. Yet we still believe in the freshness and perfection of the perfect apple – selected according to standards and criteria set by an army of corporate non-entities. The artificiality of the image of the apple could be taken as a reflection of the artifice of the marketplace shopping ‘experience’ we’re led to believe still has some semblance to our forebear’s means of hunting and gathering. Sometime later we take delivery of a perfectly formed apple. The difference between the database version and our own is so insignificant that they may as well be the same thing.
The urinal – the ‘original’ Duchampian urinal – appears in the art history continuum like the database image of the apple. The perfect version waiting to be analysed (read: consumed) by potential shoppers (read: art historians). Every version is now perfect and exactly what we ordered, in exactly the colour we requested. There is little opportunity for malfunction and serendipity in the process. Art becomes exactly what we ordered it to be. Fresh, ripe and leaving no bad taste in the mouth afterwards.
Sadly, what Duchamp missed out on was the final phase in the act of converting everyday objects into art. He should have realised that the real act of art-world transmutation was to then convert them back into everyday mass-produced objects. Thereby proving that art is merely a phase that things can pass through as and when the artist says they do. However, perhaps contextualising Rhea Myers’ project within the marketplace lends itself too easily to the idea that the artworks are for sale? It would be a mistake to imagine that the point of this project is to create a new way of purchasing and owning art. An intrinsic aspect though, is the Open Source and unrestricted dispersal of the idea and ability to create your own version. Ownership, in the traditional sense of that word, isn’t being claimed by Myers. Creating your own version means that you outright own that object. In a more traditional art environment, even though you may have contributed to a piece of work (some Fluxus projects might come to mind. Yoko Ono’s art, to name just one) you still won’t be credited with ownership or creative partnership status. The market relies on the single authorship model. Multiple unnamed authors would just get confusing and complex when copyrights start to be discussed. Locating the project within Open Source means that ownership is not claimed, but credit should be given where credit is due. When art collectors talk about merely looking after a work for the next generation, they’re talking about a continuum of ownership running through the decades. But art reduced to a commodity is saying nothing of any real value, surely?
By choosing to download and print a version for yourself you have the opportunity to own the work and be a part of that disruptive process. Owning a piece of art that comments on the past, present and future of the art world and marketplace must surely be something to desire and possess?
You can find Mark’s original article on Collaboration and Freedom – The World of Free and Open Source Art http://p2pfoundation.net/World_of_Free_and_Open_Source_Art
Part of the Furtherfield collection commissioned by Arts Council England for Thinking Digital. 2011
Featured image: Ein Identity-Workshop mit dem britischen Künstler Heath Bunting. Vertiefung Mediale Künste, Sihlquai 131, 8005 Zürich. Dienstag,
Whether Bunting is climbing trees, skateboarding, canoeing or working with technology he approaches it all with the same critical attention. He hacks around systems, physical or digital. Right from when he built his first computer at the age of 14, his life has been an experimental research project. His practice consists of a dry sense of humour and an edgy, minimal-raw aesthetic, mixed with a hyper-awareness of his own artistic persona and agency in the world, whilst engaging with complex political systems, institutions and social contexts.
Even though the subjects he explores are likely to be the most topical or important issues of the day, it always includes playfulness and an element of the prankster in his work. His work regularly highlights issues around infringements on privacy or restriction of individual freedom, as well as contexts concerning the mutation of identity, our values and corporate ownership of our cultural/national ‘ID’s’, as well as our DNA and investigations into Bio-technologies. In an age where we are submersed in frameworks and protocols designed by a neo-liberal elite for a generic consumer class, Bunting’s work is well placed as observation and practical research into the ‘depths’ of legal and illegal territories in our contemporary, networked cultures.

“our identity is constructed as human beings that can possess one or more natural persons and control one or more artificial persons. The higher up in the class system the better the access to status variety.”(Bunting)
The Status Project, is a study of the construction of our ‘official identities’ and creates what Bunting describes as “…an expert system for identity mutation”. His research explores how information the public supplies in their interaction with organisations and institutions is logged. The project draws on his direct encounters with specific database collection processes and the information he was obliged to supply as a public citizen to access specific services; this includes data collected from the Internet and information found on governmental databases. This data is then used to map and illustrate how we behave, relate, choose things, travel and move around in social spaces. The project surveys individuals locally, nationally and internationally, producing maps of “influence and personal portraits for both comprehension and social mobility”.

The use of data in contemporary life has made individuals an accessible resource for commercial and political interests. We are a rich source of data-mining material. Data mining is a process that potentially commodifies our interactions. Its historical roots lie with the development of artificial intelligence (AI) and 20th Century statistical analysis. These two methods of formulating data have grown ever closer together, backed by corporations and government-initiated military funding. Social networks such as platforms like Facebook and Internet networked institutions such as Google and the US military are all obsessed with our behaviours online. A good example is the NSA’s recent rebirth in turning most of its surveillance apparatus to spy on the US and its citizens. They have built a supercomputer tracing through billions of people’s emails, phone calls, and online activities in other countries outside of the US. The UK government is currently going through the political process of trying to implement similar spying protocols and systems to watch what UK citizens are up to.[2]
“Google suffers from data obesity and is indifferent to calls for careful preservation. It would be naive to demand cultural awareness. The prime objective of this cynical enterprise is to monitor user behaviour in order to sell traffic data and profiles to interested third parties.” [3] (Lovink)
Bunting is a Hacktivist Artist, acting (playing) out the role of a spy collecting and observing data content. Hacktivist Artists work with technology to explore how to develop their critical and imaginative practice in ways beyond the frameworks of the art establishment and its traditions. The established art arena is gradually catching up with this kind of artwork. However, one could be forgiven for thinking that many art critics and galleries are still caught in the 20th Century.
Two other artists also working on people’s data are Julian Oliver and Danja Vasiliev. They have collaborated on exploring alternative identities as the mysterious group, Men in Grey.[4] They detect online users’ vulnerabilities by tapping into and intervening in wireless network traffic – observing, tracing and copying user online activities. It is then redisplayed online on their website for others to view or transferred onto a visual screen on the side of a briefcase as an intervention in cybercafes for all to view. Although, no one knows other than themselves if the data is hacked and then redisplayed on these briefcases, as proposed in their video featuring one of their interventions. One thing is for sure – they have touched upon issues concerning our fears about personal data being seen by other people who we’d prefer were not viewing it.
The Status Project also taps into questions concerning technology, hierarchy and power. We are entwined in a complex game where the sacrifice of our information is part of connecting with others across digital networks. This raises the issue of our ‘human’ status being aligned ‘to and as’ objects of measurement. Through travel ports, our vehicles, passports, ID cards, library cards, mobile phones, alongside information about our health. We have mutated into networked (information-carrying) beings. Bunting’s own position on this matter is that “Technology is becoming more advanced and the administration of this technology is becoming more sophisticated, and soon, every car in the street will be considered and treated as persons, with human rights. This is not a conspiracy to enslave human beings, and it is a result of having to develop usable administration systems for complex relationships. Slaves were not liberated because their owners felt sorry for them; slaves were given more rights as a way to manage them more productively in a more technologically advanced society.”[5]

In the UK, in 2006 a research document called ‘A Report on the Surveillance Society For the Information Commissioner’ was published. Produced by a group of academics called the Surveillance Studies Network. This report was presented to the 28th International Data Protection and Privacy Commissioners’ Conference in London, hosted by the Information Commissioner’s Office. The publication begins by saying “Conventionally, to speak of surveillance society is to invoke something sinister, smacking of dictators and totalitarianism […] the surveillance society is better thought of as the outcome of modern organizational practices, businesses, government and the military than as a covert conspiracy. Surveillance may be viewed as progress towards efficient administration, in Max Weber’s view, a benefit for the development of Western capitalism and the modern nation-state.”[6]
We are not only under surveillance by entities we do not trust, we are also tracing each other online. Recently, in a show called ‘Being Social'[7] at Furtherfield’s new gallery, artist Liz Sterry showed her installation piece, ‘Kay’s Blog’. Sterry had “collated not only one form of online social engagements but all she could find about a Canadian blogger called Kay. Using everything from photographs to things Kay has mentioned in videos, blogs and posts on social networks, Sterry has recreated Kay’s bedroom in the gallery.”[8] (Scott)


“”There were times when I felt quite creepy,” says Liz, 28, as she shows me lists of Kay’s Facebook friends and a Google Streetview of her apartment block while a playlist of her favourite songs plays in the background.”[9]
Yet, as this ever-creeping surveillance culture grows and attaches its all seeing eyes onto us all. Whether we are referring to domestic interactions, organizational or deliberate, this is not the main issue. Neo-liberalism has developed so much now, we are all part of the Netopticon. English philosopher and social theorist Jeremy Bentham in the late Eighteenth Century designed the Panopticon. It allowed officers in institutions, particularly in prisons, to observe (-opticon) all (pan-) inmates without them knowing whether or not they are being watched. In the end it was not built, but the French philosopher Michel Foucault in his publication Discipline and Punish: The Birth of the Prison,[10] in 1975 said that we are not only monitored in prisons, but in all hierarchical structures like the army, schools, hospitals and factories. This process has evolved through history to resemble Bentham’s Panopticon. The up-dated version of Panopticon, can now be thought of as the Netopticon – where individuals are complicit in feeding their own forms of collective co-surveillance, as well as being traced by corporations, governments and spammers.

“What your data body says about you is more real than what you say about yourself. The data body is the body by which you are judged in society, and the body which dictates your status in the world. What we are witnessing at this point in time is the triumph of representation over being. The electronic file has conquered self-aware consciousness.” [11] (Critical Art Ensemble)
So far, for the project he has created a functioning, sketch database of the UK system with over 10,000 entries – made over 50 maps of sub-sections of the system to aid sense of place and potential for social mobility. Bunting says he is also researching how to convert his identity generating software into a bot recognised under UK law as a person “covered by the human rights act i.e. right to life and liberty; freedom of expression; peaceful enjoyment of property. I am very close to achieving this.”
This bring us to another part of the project what I call ‘Identity Kits’, and Bunting calls ‘Synthetic off-the-shelf (OTS) British natural person’.[12] These kits consist of various items, personal business cards, library cards, a national railcard, t-mobile top-up card, national lottery card and much more. They take a few months to compile each of them because they are actual items that everybody uses in their everyday lives, involving evidence of identity. There is also a charge for the package of 500.00 GBP, which is cheap for a new identity.

Bunting stresses that these UK identities are lawful and that there is no need for any official consulting or permission from an authority to use or make them. Through this he intends to illustrate a precise codification of class in the UK system. Currently, he defines three classes of identitiy: human being, person and corporate. What class of individual you are places you into categories of evaluation, this process allows others to judge your status, worth and value, within a hierarchy, which is clearly represented in the status maps.
This work touches on issues around our everyday status as a critique, but also as an investigative hack, and plays around with the quagmire of inequality currently in the UK. Inequality is built, constructed into the fabric our societies as an accepted default, through tradition, social or mechanistic, holding in place societal divisions. If there was a status project made in other countries reflecting their own status, worth and value of citizens there would be clear links defining where the connections and divisions lie, between each culture. In fact, another project worth mentioning here is ‘The Spirit Level: Why More Equal Societies Almost Always Do Better’. [13] The authors Richard Wilkinson and Kate Pickett have done their own ‘extensive’, detailed research in highlighting through many different graphs, mapping out inequality around ther globe.
“We know there is something wrong, and this book goes a long way towards explaining what and why.” [14] (Hanley)
Bunting’s work expresses a discipline conscious of agency, autonomy and enactments for self and collective empowerment. Hacking different routes around what at first is seen as too big to deal with, lessens its power and awe. Like Burbank in the ‘The Truman Show’, what we have been told is not real. Bunting knows this instinctively, and is on a quest to upturn each stone to see what lies beneath. But at the same time these facilities created to crack the social, and data orientated codes, are shared. He then leaves the paths he has discovered wide open for others pass through, as we all struggle to survive the ever creeping strangle-hold, of the Netopticon.
———————————————————————-
This article was written for and will be published as part of Heath Bunting’s presentation in Athens ‘Workshop How to Build a New Legal Identity’, May 5th 2012.
During the workshop, Heath Bunting will introduce us to techniques and strategies on how to form new identities. The distribution of the workshop How to Build a New Legal Identity across Europe aims at exploring the characteristics of identity in each country.
Artist’s Talk: May 4, 2012 @ 19.00
Workshop How to Build a New Legal Identity: May 5, 2012 @ 12.00
Frown Tails, 6 Paramythias str, Keramikos, Athens
Organised by: Katerina Gkoutziouli and Frown Tails
“It is not accidental that at a point in history when hierarchical power and manipulation have reached their most threatening proportions, the very concepts of hierarchy, power and manipulation come into question. The challenge to these concepts comes from a redsicovery of the importance of spontaneity – a rediscovery nourished by ecology, by a heightened conception of self-development, and by a new understanding of the revolutionary process in society.” Murray Bookchin. Post-scarcity and Anarchism (1968).
The rise of neo-liberalism as a hegemonic mode of discourse, infiltrates every aspect of our social lives. Its exponential growth has been helped by gate-keepers of top-down orientated alliances; holding key positions of power and considerable wealth and influence. Educational, collective and social institutions have been dismantled, especially community groups and organisations sharing values associated with social needs in the public realm. [1] Bourdieu.
In this networked society, there are controversies and battles taking place all of the time. Battles between corporations, nation states and those who wish to preserve and expand their individual and collective freedoms. Hacktivist Artists work with technology to explore how to develop their critical and imaginative practice in ways that exist beyond traditional frameworks of art establishment and its traditions. This article highlights a small selection of artists and collaborative groups, whose work is linked by an imaginative use of technology in order to critique and intervene into the opressive effects of political and social borders.
In June 2000, Richard Stallman [2] when visiting Korea, illustrated the meaning of the word ‘Hacker’ in a fun way. When at lunch with some GNU [3] fans a waitress placed 6 chopsticks in front of him. Of course he knew they were meant for three people but he found it amusing to find another way to use them. Stallman managed to use three in his right hand and then successfully pick up a piece of food placing it into in his mouth.
“It didn’t become easy—for practical purposes, using two chopsticks is completely superior. But precisely because using three in one hand is hard and ordinarily never thought of, it has “hack value”, as my lunch companions immediately recognized. Playfully doing something difficult, whether useful or not, that is hacking.” [4] Stallman
The word ‘hacker’ has been loosely appropriated and compressed for the sound-bite language of film, tv and newspapers. These commercial outlets hungry for sensational stories have misrepresented hacker culture creating mythic heroes and anti-heroes in order to amaze and shock an unaware, mediated public. Yet, at the same time hackers or ‘crackers’ have exploited this mythology to get their own agendas across. Before these more confusing times, hacking was considered a less dramatic activity. In the 60s and 70s the hacker realm was dominated by computer nerds, professional programmers and hobbyists.
In contrast to what was considered as negative stereotypes of hackers in the media. Steven Levy [5], in 1984 published Hackers: Heroes of the Computer Revolution [6]. In three parts, he writes about the canonical AI hackers of MIT, the hardware hackers who invented the personal computer industry in Silicon Valley, and the third-generation game hackers in the early 1980s. Yet, in this publication, what has had the most impact on hacker culture and is still used widely as a guideline by many is the ‘hacker ethic’. He identified this Hacker Ethic to be a code of practice consisting of key points such as that “all information is free”, and that this information should be used to “change life for the better”.
1. Access to computers—and anything which might teach you something about the way the world works—should be unlimited and total. Always yield to the Hands-on Imperative!
2. All information should be free.
3. Mistrust authority—promote decentralization.
4. Hackers should be judged by their hacking, not bogus criteria such as degrees, age, race or position.
5. You can create art and beauty on a computer.
6. Computers can change your life for the better.
Levy’s hacker ethic promotes the idea of performing a duty for the common good, an analogy to a modern day ‘Robin Hood'[ibid]. Proposing the concept that hackers are self-reliant whilst embracing a ‘healthy’ anti-authoritarian stance, combined with free and critical thinking. Proposing that hackers should be judged by their ability to hack, and presenting hacking as an art-form. Levy also says that the Free and open source software (FOSS) movement is the descendant of the hacker ethic. However, Levy’s hacker ethic has often been quoted out of context and misunderstood as to refer to hacking as ‘breaking’ into computers. This specifically prescribed role, denies the wider and creative context of what hacking is and could be. It does not have to be just about computer security.
This leads us to ‘crackers’. All crackers hack and all hackers hack. But, crackers are seen as second rate wannabe hackers by the older generation of hackers. The Black Hat Hacker or cracker designs and releases malicious code, gathers dangerous information and brings down sensative systems. The White Hat Hacker hunts down and destroys malicious code, and the casual hacker who hacks in order to learn information for his or her own curiosity; both generally dislike ‘Black Hats’ and ‘Crackers’, and tend to view them as computer criminals and dysfunctional juveniles. Lately, crackers have also been labeled as ‘script kiddies’. As a kind of snobbish insult, it refers to those who are not capable of building or programming their own tools, but tend to use scripts and programs written by others to perform their intrusions. To add to the confusion we also have the term ‘Grey hat’. Which refers to a hacker acting between black hat and white hat. Indeed, this could demonstrate where art hacktivists reside, challenging the trappings of the traditional concept of goody and baddy.
“There is another group of people who loudly call themselves hackers, but aren’t. These are people (mainly adolescent males) who get a kick out of breaking into computers and phreaking the phone system. Real hackers call these people ‘crackers’ and want nothing to do with them.” [7] Raymond.
“The basic difference is this: hackers build things, crackers break them.” [ibid] Raymond.
But before we judge,
let’s view a snippet of the \/\The Conscience of a Hacker/\/ by +++The Mentor+++
Written on January 8, 1986.[8]
“This is our world now… the world of the electron and the switch, the
beauty of the baud. We make use of a service already existing without paying
for what could be dirt-cheap if it wasn’t run by profiteering gluttons, and
you call us criminals. We explore… and you call us criminals. We seek
after knowledge… and you call us criminals. We exist without skin color,
without nationality, without religious bias… and you call us criminals.
You build atomic bombs, you wage wars, you murder, cheat, and lie to us
and try to make us believe it’s for our own good, yet we’re the criminals.”
The term ‘Hacktivism’ was officially coined by techno-culture writer Jason Sack in a piece about media artist Shu Lea Cheang published in InfoNation in 1995. Yet, the Cult of the Dead Cow [9] are also acknowledged as defining the term. The Cult of the Dead Cow are a group of hackers and artists. They say the Hacktivism phrase was originally intended to refer to the development and use of technology to foster human rights and the open exchange of information.
Hacktivism techniques include DoS attacks, website defacement, information theft, and virtual sabotage. Famous examples of hacktivism include the recent knocking out of the PlayStation Network, various assistances to countries participating in the Arab Spring, such as attacks on Tunisian and Egyptian government websites, and attacks on Mastercard and Visa after they ceased to process payments to WikiLeaks.
Hacktivism: a policy of hacking, phreaking or creating technology to achieve a political or social goal.
“Hacktivism is a continually evolving and open process; its tactics and methodology are not static. In this sense no one owns hacktivism – it has no prophet, no gospel and no canonized literature. Hacktivism is a rhizomic, open-source phenomenon.” [10] metac0m.
The practice or behaviour of Hacktivism is at least as old as Oct 89 when DOE, HEPNET and SPAN (NASA) connected to (virtual) networked machines world wide. They were penetrated by the anti-nuclear group WANK worm.
WANK penetrated these machines and had their login screens altered to…
HACKING BORDERS: Examples of Art Hacktivism & Cultural Hacking…

“Radical groups are discovering what hackers have always known: Traditional social institutions are more vulnerable in cyberspace than they are in the physical world. And some members of the famously sophomoric hacker underground are becoming motivated by causes other than ego gratification.” [11] Harmon.
Hacktivism, exploits technology and the Internet, experimenting with the immediacy of distributable networks as a playful medium for independent, creative and free expression. There has been a gradual and natural shift from net art (and net.art) into Hacktivism. Net Art in spirit, has never really been just about art being viewed on a web browser alone. Some of the very same artists whose artwork involved being shown in browsers and making code behind the browser as part of the art, have also expanded their practice outside of the browser. One such artist is Danja Vasiliev, “Fifteen years ago WWW was something very new in Russia and besides the new dial-up aesthetics and world-wide means it brought a complete new layer of existence – “netosphere”, which made my youth.” Vasiliev very soon moved on from playing with browsers into a whole new territory. [12]
Danja co-founded media-lab moddr_ in 2007, a joint project at Piet Zwart Institute alumni and WORM Foundation. Based in Rotterdam moddr_ is a place for artists and hackers, engaging with critical forms of media-art practice. He collaborated with Gordan Savicic and Walter Langelaar from the moddr.net lab on the project Web 2.0 Suicide Machine, which lets you delete your social networking profiles and kill your virtual friends, and it also deletes your own profile leaving your profile image replaced by a noose.”The idea of the “Web 2.0 Suicide Machine” is to abandon your virtual life — so you can get your actual life back, Gordan Savicic tells NPR’s Mary Louise Kelly. Savicic is the CEO — which he says stands for “chief euthanasia officer” — of SuicideMachine.org.” [13]

Just like another project called ‘Face to facebook’ that stole 1 million facebook profiles and re-contextualized them on a custom made dating website (lovely-faces.com), set up by Italian artists Paolo Cirio and Alessandro Ludovico, whom also just so happens to be editor in chief of Neural magazine. Web 2.0 Suicide Machine, had to close its connections down regarding its Facebook activities after receiving a cease and decease letter from Facebook. [14]
Julian Oliver and Danja Vasiliev teamed up and formed the mysterious group Men in Grey. The Men In Grey explore our online vulnerabilities by tapping into, intervening into wireless network traffic. Observing, tracing and copying what we do. This hack then redisplays our activities back to us, showing the data of our online interactions.
At first no one (except myself & a few others) knew who they were. When they first arrived on the scene I started an interview with them and then suddenly, I was asked to hold back due to their antics on the Internet and interventions in public environments receiving much coverage. They were not sure how it would pan out for them. Partly due to the anonymous nature of their project, and also because of the sudden impact of the larger hacktivist group Anonymous getting much press in commercial media themselves.
“Men In Grey emerge as a manifestation of Network Anxiety, a fearful apparition in a time of government wiretaps, Facebook spies, Google caches, Internet filters and mandatory ISP logging.” M.I.G
“Spooks are listening into calls, just like they always have,” said Eric King of London’s Privacy International, in an e-mail. “With A5/1 being broken—you can decrypt and listen into 60 calls at once with a box smaller than a laptop.” [15]
Later they won the Golden Nica (1st prize) Interactive Arts category, Prix Ars Electronica in 2011. In a show called Project Space — M.I.G. — Display of unknown, quarantined equipment hosted at the Aksioma Project Space Komenskega, Ljubljana 2011. The statement read:
“The particularly threatening quality of the Men In Grey equipment is its apparently invasive nature; it seems able to penetrate – and even hack into – virtually any electronic device in its reach. While we are all aware of the wire-tapping and data retention done by the government (along with the spying carried out by corporations like Facebook and Google), Men In Grey seem to operate with a range of tools and techniques well beyond those that are currently known to be in use.”

Hacktivism involves many different levels of social intervention and engagement. Whether it is to do with direct action, self-referential geekiness, obscure networked antics, crtical gaming, or peer 2 peer and collective change. Hacktivists challenge defaults put in place by other people, usually the systems imposed upon them and the rest of us by authority. Even though the subjects themselves may be concerning serious matters, humour and playfulness are both essential ingredients.
“A promising tactic for the early Situationists was the unpredictable yet forceful potential of play — what anthropologist Victor Turner termed the “liminoid,” or the freeing and transformational, moments of play when the normal roles and rules of a community or society are relaxed.” [16] Dovey & Kennedy.
One group crossing over from the digital into physical and social realms, is Tiltfactor. [17] Their form of intervention is not necessarily about causing political controversy, but is engaged in reaching people through games of play. Experimenting with social everyday contexts, making games that tackle less traditional topics, such as public health, layoffs, GMO crops. One of the many games creating awareness on these subjects, is POX “Our game actually helps a player understand how a disease can spread from one place to another and how an outbreak might happen” says Mary Flanagan. [18]
A local public health group called Mascoma Valley Health in the New Hampshire region of the US approached Tiltfactor with the problem of the lack of immunization. “At first, a game about getting people immunized seemed like one of the most “un-fun” concepts imaginable. But that sinking feeling of impossibility almost always leads to good ideas later.” [19] Flanagan.

“Geopolitical space has always been a conflicted and fragile topic. Borders and frontiers are changing so fast, that sometimes it seems that our sociopolitical status can change from “citizen” to “immigrant” from one moment to another, or simply live under the “immigrant” status all your life. We’re getting used to words like refugees, enclaves, war, borders, limits –and the list has no end.” Ethel Baraona Pohl & César Reyes

Ricardo Dominguez collaborated with Brett Stalbaum, Micha Cardenas, Amy Sara Carroll & Elle Mehrmand, on (TBT) (and others), on a hand-held mobile phone device that aids crossers of the Mexico-US border. An inexpensive tool to support the finding of water caches left in the Southern California desert by NGO’s for those crossing the border.
“The entire group of artists who are part of Electronic Disturbance Theater 2.0/b.a.n.g. lab working on the Transborder Immigrant Tool (TBT) was being investigated by UCSD and 3 Republican Congressmen starting on January 11, 2010. Then I came under investigation for the virtual sit-in performance (which joined communities statewide against the rising students fees in the UC system and the dismantling of educational support for K–12 across California) against the UC Office of the President (UCOP) on March 4, 2010. This was then followed by an investigation by the FBI Office of Cybercrimes.” [20] Ricardo Dominguez.

In an interview with Lawrence Bird Dominguez discusses that the TBT is still developing as a gps tool, but infers that it is not just a tool but also ‘border disturbance art’, consisting of different nuances existing as part of a whole with other factors at play. Such as a hybrid mix of things, objects and expressions “artivism, tactical poetries, hacktivism(s), new media theater, border disturbance art/technologies, augmented realities, speculative cartographies, queer technologies, transnational feminisms and code, digital Zapatismo, dislocative gps, intergalactic performances, [add your own______].” [ibid]
“Borders are there to be crossed. Their significance becomes obvious only when they are violated – and it says quite a lot about a society’s political and social climate when one sees what kind of border crossing a government tries to prevent.” [21] Florian Schneider

National borders are front-lines of political and social friction. The exerience of asylum-seekers and political migrants reflect some of the most significant issues of our time. Immigration is a toxic issue and unpopular with voters. Bunting’s BorderXing Guide, plays on the fear of invisible alien hordes of people crossing our borders illegally.
The context of this work fits well with issues about borders, whether it is about creating borders online or physical environments. Only those needing to cross a border are allowed access to the site, it is limited to ‘social clients’ who have a static IP (Internet Protocol) address and who, most notably, have gained the artist’s confidence. Such as peer activists and immigrants using libraries, colleges, cultural centres. The site allows those who would other wise end up crossing borders in harmful ways, such as in containers, on the backs of (and underneath) lorries and planes.
Heath Bunting’s BorderXing Guide website primarily consists of documentation of walks that traverse national boundaries, without interruption from customs, immigration, or border police. The work comments on the way in which movement between borders is restricted by governments and associated bureaucracies. It is a manual written not at distance like a google map, but by foot. A physical investigation, involving actually going to these places; trying these discovered routes out and then sharing them with others. A carefully calculated politics of public relations.
“The Feral Trade Café is more than just an art space that’s a working café, it’s about provoking people to question the way big food corporations operate by looking at the journey of the food we end up scraping into our pampered bins.” [22] Gastrogeek
Feral Trade uses social and cultural hand baggage to transport food based items between cities, often using other artists and curators as mules. Feral Trade products (2003-present), alongside ingredient route maps, bespoke food packaging, video and other artefacts from the Feral Trade network. The goods rangefrom coffee from El Salvador, hot chocolate from Mexico and sweets from Montenegro, as well as locally sourced bread, vegetables and herbs.
Kate Rich uses the word ‘feral’ as a process refering to being deliberately wild, as in pigeon, as opposed to romantic nature wild as the wolf. It is an unruly wild, shitting everywhere, disruption and annoyance in contrast to ‘official’ human structures and connected infrastructures. Feral Trade freight operates largely outside commercial channels, using the surplus potential of social, cultural and data networks for the distribution of goods. Working with co-operatives, small growers and food producers.
The Feral Trade Courier is a live shipping database for a freight network running outside commercial systems. The database offers dedicated tracking of feral trade products in circulation, archives every shipment and generates freight documents on the fly.

Every shipment is different and has its own story of how and where it was delivered from. Also included is information on who the carriers are with details about producers and their local culture as contextual information. The product packaging itself is also a carrier of information about social, political context and discussions with producers and carriers.
![Feral Trade at Furtherfield's Gallery (2009) [23] Link to exhibition](http://www.furtherfield.org/wp-content/uploads/2012/03/3657297700_42b1c26014_b.jpg)
Since the rise of the Internet individual and collective actions are symbiotically connected to the every day. In a world transformed, common people have access to tools that can change ‘our’ cultures independently; sharing information, motivating actions and changing situations. We know of the Arab Spring, the Occupy movement, Anonymous and Wikileaks and how successful they have been in exploiting technology and social networks. Technology just like any other medium is a flexible material. By tweaking, breaking and remaking ‘something’ you can re-root it’s function, change its purpose.
The links between these mass social movements and the artists here are not just relating to technology’s use but, a shared critique at the same enemy, neo-liberalism.
“”Neo-liberalism” is a set of economic policies that have become widespread during the last 25 years or so. Although the word is rarely heard in the United States, you can clearly see the effects of neo-liberalism here as the rich grow richer and the poor grow poorer.” [24] Martinez & Garcia.
At the same time as highlighting the continual privatization of human society. This form of art practice shows us the cracks of where a social divide of gate-keeping has maintained power within the Western World’s, traditional art structures. We now realize that the art canons we have been taught to rely on as reference are more based around privelage, centralization and market dominance rather than democratic representation or even just pure talent. Hacktivist artists adapt and recontextualize with a critical approach, towards a larger and more inclusive context beyond their own immediate selves. Demonstrating a respect and use of autonomy, and an awareness of social contexts and political nuances, freeing up dialogue for new discussions which include a recognition of social contexts, as a vital ingredient and valued resource in art. Re-aligning, reconfiguring the defaults of what art is today.
Face to facebook is the final project in a three part series named “Tha Hacking Monopolism Triology” by the two Italian artists Paolo Cirio and Alessandro Ludovico. It was launched on the 2nd February 2011, with a mixed media installation at the Transmediale festival in Berlin, and a press release announcing a new dating website called lovely-faces.com.
The set-up for the ‘Face to facebook’ project was to steal 1 million facebook profiles and re-contextualize them on a custom made dating website (lovely-faces.com). The data collected from the profiles was only information available publicly on the internet, like the users name and profile picture. No facebook account was needed to access it. The 1 million facebook profile pictures were then checked for images that were usable in a dating webstie context. The remaining 250,000 profile pictures were then fed through various face recognition filters to assign an assumed personality to the subjects and a new profile was created ready for the dating website. Once published on lovely-faces.com, interested pursuers could get in contact with the people behind the original facebook profiles through facebook messages.
On the 10th February, 8 days after its launch, the dating website lovely-faces.com was shut down. This was following a cease and decease letter from Facebook[1]. Back in 1999, the net artist Heath Bunting was also subject to a cease and decease letter, that time from American Express. The letter sent to Paolo Cirio and Alessandro Ludovico in 2011 (as PDF) can be seen here, and the letter sent to Heath Bunting in 1999 is published here.
This project, and the ripples it left on the media water, highlights an ambiguous relationship many have with facebook. Many people sign up, upload a smiling profile picture of themselves and declare personal details to the large corporation that is Facebook without concern. Not until these identities and personal images were scavenged and then reused, the ownership and potential audience of this personal data is questioned. As the artists state themselves: “The final step is to be aware that almost everything posted online can have a different life if simply recontextualized. “
“The process is always illustrated in a diagram that shows the main directions and processes under which the software has been developed. We found a significant conceptual hole in all of these corporate systems and we used it to expose the fragility of their omnipotent commercial and marketing strategies. In fact all these corporations established a monopoly in their respective sectors (Google, search engine; Amazon, book selling; Facebook, social media), but despite that their self-protective strategies are not infallible. And we have been successful in demonstrating this.”
Web 2.0 Suicide machine (http://suicidemachine.org/) is another project which deals with your online identity. It allows you to automatically delete all your social network profiles and it simplifies the process – according to their website 8.5h quick then a manual deletion. Incidentially, the facebook is not one of the profiles subject to deletion in the suicide machine anymore, following another cease and decease letter: http://suicidemachine.org/download/Web_2.0_Suicide_Machine.pdf.

Since the lovely-faces.com dating website is still closed down, the project now (September 2011) consists of: documentation of the process used to acquire the facebook profiles; documentation of the global mass media hack performance, in the form of news broadcasts, magazine articles and blog post referring to the project; legal correspondence between the lawyers of the artists and Facebook; a mixed media installation; a touring lecture given by the authors. The latter two being re-performed and installed in various venues around Europe and beyond. The former are all available on the website face-to-facebook.net
The ever changing nature of this project therefore makes it a great example of a piece of contemporary art of variable nature, one which is in constant flux and is formed by the cultural, networked and physical landscape surrounding it. It does not only challenge the ownership of your online identity, it is also a nuisance for a mainstream contemporary art market based on institutional preservation and commercial commodification. These disruptions may also be linked. On the one hand there is an action to copy a system collecting and commodfying people and then use them as assets in one’s art expression and experience. “In all the three projects, the theft is not used to generate money at all, or for personal economic advantage, but only to twist the stolen data or knowledge against the respective corporations.” And then on the other hand, it is an art project which is not straightforward to see what the remaining artefacts actually are, whilst defying the process of being added to traditional art collections.
Other Info:
The Hacking Monopolism Trilogy. Face to Facebook is the third work in a series that began with Google Will Eat Itself and Amazon Noir. http://www.face-to-facebook.net/hacking-monopolism-trilogy.php
Elin Ahlberg is studying Art and Visual culture at the University of the West of England in Bristol. She has been living in the UK, and Bristol, since her move from Sweden in 2006. As an artist, she works in a variety of mediums and produces work which aims to both amuse and provoke. Her practice and research is informed by quasi-anthropological observations and an interest in technology. “One year ago I gave up Facebook for lent. It was quite an interesting experiment and I realised how integrated my life was with the social networking website as I actually felt that I missed out on things.” Ahlberg’s essay Meanings constructed around Facebook can be found here http://elinahlberg.wordpress.com/2011/07/18/essay-meanings-constructed-around-facebook-2011/
“Does Lara Croft Wear Fake Polygons?” that was the question Anne-Marie Schleiner (http://www.opensorcery.net) asked in a gender analysis essay of the popular videogame Tomb Raider published year 2000 in the Switch magazine.
The videogame Tomb Raider was released by Core Design in 1996 and the heroine a British archaeologist named Lara Croft did not only have big guns but also big breasts. In a couple of years she became a well known character not only in the games world but also for the general public when she entered the silvercreen, played by Angelina Jolie. You could say that Lara Croft is the Mona Lisa of the game world, beautiful, mysterious and well known for a large audience outside the games world.

In her essay Anne-Marie Schleiner mentions the famous Nuderaider patch, a game add-on that strips Lara Croft’s clothing so you could play her naked.
The artist Robert Nideffer’s Nuderaider patch made in 1999 consisted of three-parts:
1) an appropriated website where he repurposed the existing commercial site
2) a spoofed mail-server that re-routed messages submit to Lara Croft fan club website to the Director of development at Eidos UK as if it were coming from the Director of Marketing in the US branch
3) a patched version of the Nude Raider patch, which placed police blotter style bar codes across Lara’s private parts (and gave her a goatee as a Duchampian homage), thwarting the game player’s expectation of seeing her polygonal private parts.
“This shows the male dominancy within the game world by having a female lead appearing like a super model. By presenting her naked, it makes the game seem satirical just pushing the creators’ ideas a little further.” Nideffer [2]
In 1919 the artist Marcel Duchamp used a cheap postcard-sized reproduction of Leonardo da Vincis famous painting Mona Lisa on which he drew a moustache and a goatee, in the same way Nideffer later did with Lara Croft. Duchamp called his work L.H.O.O.Q a titled that pronounced in French should be “Elle a chaud au cul”, which translated to English means “She has a hot ass”.
Eidos sent cease and desist letters to the owners of nuderaider.com who were hosting the Nude Raider patch, enforcing their copyright of Tomb Raider.[3]


In the machinima “She Puppet” from 2001, the American artist Peggy Aswesh also investigates the gender and cultural identities of Lara Croft by mixing scenes from the Tomb Raider game. Aswesh describes Croft as a virtual girl-doll of the late 20th century, perhaps boy-doll would be a better description since most of the player of the early Tomb Raider games were men or boys. In her essay Schleiner makes the observation that Lara Croft is a “well-trained techno-puppet created by and for the male gaze.” It’s obvious that the videogame Tomb Raider has played a major role in stirring up emotions with its out of date and suspect attitude towards women. But Lara Croft has not only been a subject for critically engaged, artistic gender discussions.

The artists Marieke Verbiesen has created the game Tombraider 0.1 in which she flattened the 3D game into a 2D-world and borrowed aesthetic from the early game consoles. In the new game you could also find references to classic computer gaming experiences such as the stuck “loading” screen, bad language translations and space-invader attacks. It is not unusually that artist create copies of videogames, with 3D hyperrealism graphic, in a retro old-fashioned style.

Another way to do this is to use pixel-graphic. That is exactly what Arno Coenen, Rob Coenen and, Rene Bosma did when they re-created he 3D game character into a 2D experience with a touch of pixel-feeling. The project Output: 62.500 materialized pixels, used 62.500 pieces to create a floor mosaic measuring 5,25 x 5,25 meters of the videogame icon Lara Croft. The mosaic has been exhibited at different places in Amsterdam and Kiasma at the Alien Intelligence exhibition in 2000.
So fake polygons or not, it looks like Lara Croft has not only made an impression in the history of videogames but also in the history of art.
Tombraider 0.1 – Single-player game installation based on the famous 3d game Tombraider, starring the female fightingmachine Lara Croft. http://www.marieke.nu/tombraider01/eng/
MUTATION.FEM. Anne-Marie Schleiner “An Underworld Game Patch Router to Female Monsters, Frag Queens and Bobs whose first name is Betty” http://www.opensorcery.net/mutation/