

In “How Readers Will Discover Books In Future“, science fiction author Charles Stross envisions a future in which weaponized eBooks demand your attention by copying themselves onto your mobile devices, wiping out the competition, and locking up the user interface until you’ve read them.
This is only just science fiction. Even the earliest viruses often displayed messages and malware that denies access to your data until you pay to decrypt it already exist. ePub ebooks can execute arbitrary JavaScript, and PDF documents can execute arbitrary shell scripts. Compromised PDFs have been found in the wild. Stross’s weaponized ebooks are not more than one step ahead of this.
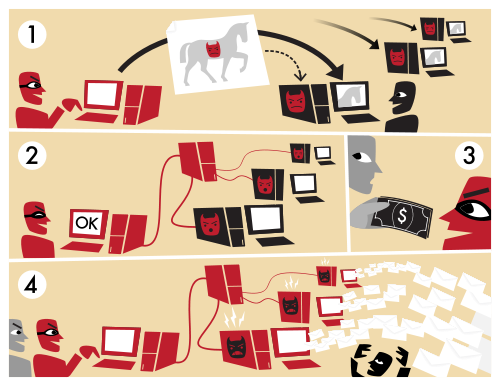
Why would eBooks want to act like that? To find readers. In the attention economy, the time required to read a book is a scarce resource. Most authors write because they want to be read and to find an audience. Stross’s proposal is just an extreme way of achieving this. In Stross’s scenario, authors are like the criminal gangs that use botnet malware to get your computer to pursue their ends rather than your own, use adware to coerce you into performing actions that you wouldn’t otherwise, or use phishing attacks to get scarce resources such as passwords or money from users.
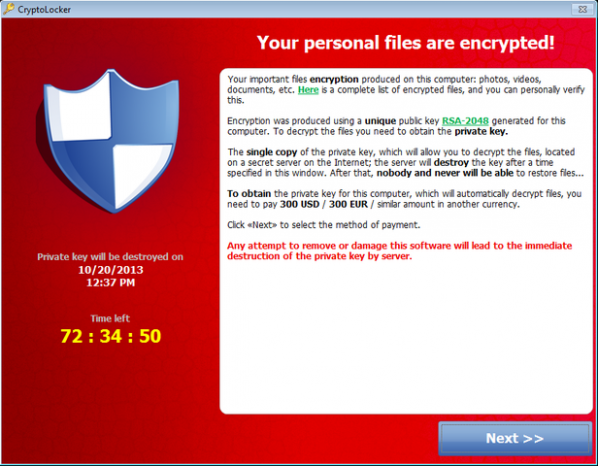
As so much new art is made that even omnivorous promotional blogs like Contemporary Art Daily cannot keep up, scarcity of attention becomes a problem for art as well as for literature. And when people do visit shows they spend more time reading the placards than looking at the art. In these circumstances Stross’s strategies make sense for art as well. Particularly for net art and software art.
A net or software artwork that acted like Stross’s vampire eBooks would copy itself onto your system and refuse to unlock it until you have had time to fully experience it or have clicked all the way through it. It could do this in web browsers or virtual worlds as a scripting attack, on mobile devices as a malicious app, or on desktop systems as a classical virus.
Unique physical art also needs viewers. Malicious software can promote art, taking the place of private view invitation cards. Starting with mere botnet spam that advertises private views, more advanced attacks can refuse to unlock your mobile device until you post a picture of yourself at the show on Facebook (identifying this using machine vision and image classification algorithms), check in to the show on FourSquare, or give it a five star review along with a write-up that indicates that you have actually seen it. In the gallery, compromised Google Glass headsets or mobile phone handsets can make sure the audience know which artwork wants to be looked at by blocking out others or painting large arrows over them pointing in the right direction.

Net art can intrude more subtly into people’s experiences as aesthetic intervention agents. Adware can display art rather than commercials. Add-Art is a benevolent precursor to this. Email viruses and malicious browser extensions can intervene in the aesthetics of other media. They can turn text into Mezangelle, or glitch or otherwise transform images into a given style. In the early 1990s I wrote a PostScript virus that could (theoretically) copy itself onto printers and creatively corrupt vector art, but fortunately I didn’t have access to the Word BASIC manuals I needed to write a virus that would have deleted the word “postmodernism” from any documents it copied itself to.

Going further, network attacks themselves can be art. Art malware botnets can use properties of network topography and timing to construct artworks from the net and activity on it. There is a precursor to this in Etoy’s ToyWar (1999), or EDT’s “SWARM” (1998), a distributed denial of service (DDOS) attack presented as an artwork at Ars Electronica. My “sendvalues” (2011) is a network testing tool that could be misused, LOIC-style, to perform DDOS attacks that construct waves, shapes and bitmaps out of synchronized floods of network traffic. This kind of attack would attract and direct attention as art at Internet scale.

None of this would touch the art market directly. But a descendant of Caleb Larsen’s “A Tool To Deceive And Slaughter” (2012) that chooses a purchasor from known art dealers or returns itself to art auction houses then forces them to buy it using the techniques described above rather than offering itself for sale on eBay would be both a direct implementation of Stross’s ideas in the form of a unique physical artwork and something that would exist in direct relation to the artworld.
Using the art market itself rather than the Internet as the network to exploit makes for even more powerful art malware exploits. Aesthetic analytics of the kind practiced by Lev Manovich and already used to guide investment by Mutual Art can be combined with the techniques of stock market High Frequency Trading (HFT) to create new forms by intervening in and manipulating prices directly art sales and auctions. As with HFT, the activity of the software used to do this can create aesthetic forms within market activity itself, like those found by nanex. This can be used to build and destroy artistic reputations, to create aesthetic trends within the market, and to create art movements and canons. Saatchi automated. The aesthetics of this activity can then be sold back into the market as art in itself, creating further patterns.
The techniques suggested here are at the very least illegal and immoral, so it goes without saying that you shouldn’t attempt to implement any of them. But they are useful as unrealized artworks for guiding thought experiments. They are useful for reflecting on the challenges that art in and outside the artworld faces in the age of the attention-starved population of the pervasive Internet and of media and markets increasingly determined by algorithms. And they are a means of at least thinking through an ethic rather than just an aesthetic of market critique in digital art.
The text of this article is licenced under the Creative Commons BY-SA 4.0 Licence.